TCP SYN Flood attacks are the most popular ones among DDOS attacks. Here we will discuss, in detail, the basis of the TCP SYN attack and to stop it before it reaches those servers.
It’s been more than two decades since the first DDOS attack was attempted at the University of Minnesota, knocking it down for two days. A lot followed that, including one of the biggest in the history of DDOS, which was against Github and involved a 1.35 TBps attack against the site.
DOS attacks pose severe threats to servers and websites by flooding the targeted servers with bogus traffic, denying legitimate traffic access.
How the SYN Attack Works
TCP SYN attack is one of the most popular DDOS attacks, which target the hosts that run TCP processes and exploit the normal TCP three-way handshake process.
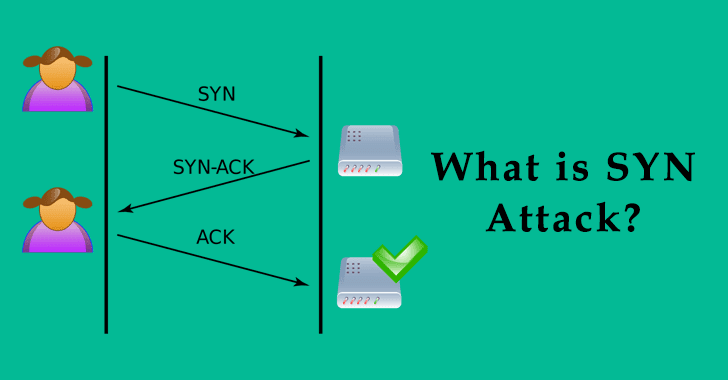
In a normal TCP scenario, communication between the client and server begins after establishing a virtual connection. The client initiates a connection by sending SYN requests to Server, and Server then responds back by sending SYN/ACK.
This SYN/ACK is an acknowledgment of the initial SYN request from the client. The client responds by ACK packet, completing the connection to start communication.
In a DDOS environment, a malicious actor spoofs the Client and sends excessive SYN requests from random IP addresses to the targeted server.
The server, assuming it to be legitimate requests responds with SYN/ACK, but never receives a final ACK back, thus tying up the Server’s resources with half-open TCP sessions which eventually leads to denying the legitimate connection requests.
How to Prevent SYN Flood Attack
SYN Cookies
Unlike normal TCP handshakes, it works by avoiding the need to maintain a state table for all TCP half-open connections. This method employs the use of cryptographic hashing. The server crafts the ISN (Initial Sequence Number) along with the initial SYN-ACK flood sent to the client.
This ISN is calculated based on Source IP, Destination IP, port numbers, and a secret number. When the server receives ACK from the Client, it validates it for its legitimacy by checking if the incremented ISN matches and then allocating memory for the connection.
Increasing Backlog Queue
Each Operating System allocates memory to half-open connections and there is a limit to the number of these connections it can hold. Once that limit is achieved, it starts dropping off the connection.
In the case of the SYN attack, the limit of the backlog can be increased and would prevent the dropping of legitimate connections.
Firewall Filtering
Firewall filtering can be enabled on the firewall to detect and prevent these SYN attacks. For example, the source threshold can be changed. In this case, a particular threshold can be set up before the firewall drops connections from one source.
It is important to note that, unlike other attacks, SYN attack doesn’t require robust systems; all the attacker need is a PC with a dial-up connection to launch high-impact attacks.
Copyright 2021 Associated Press. All rights reserved.