Cyber Security
Zero Trust Data Access (ZTDA) constitutes a fundamental aspect of the wider Zero Trust security framework, which entails limiting data access. The Zero Trust security approach...
Hi, what are you looking for?

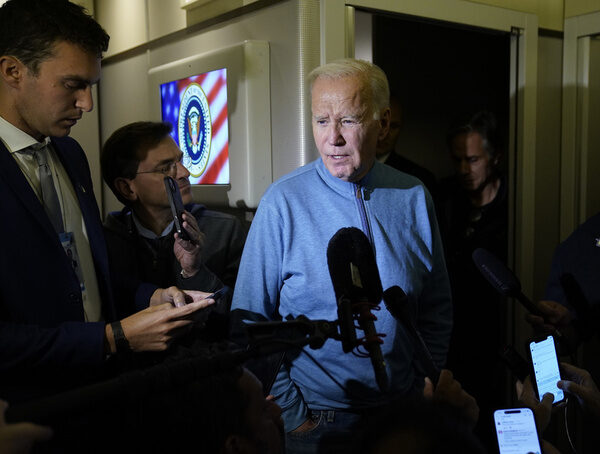
WASHINGTON (AP) — As the 3-week-old Israel-Hamas war enters what Israeli Prime Minister Benjamin Netanyahu says could be a “long and difficult” new stage, President Joe Biden is calling on Israeli and...
KHAN YOUNIS, Gaza Strip (AP) — Two days after cellular and internet service abruptly vanished for most of Gaza amid a heavy Israeli bombardment, the...
DEIR AL-BALAH, Gaza Strip (AP) — Thousands of people broke into aid warehouses in Gaza to take flour and basic hygiene products, a U.N....
Zero Trust Data Access (ZTDA) constitutes a fundamental aspect of the wider Zero Trust security framework, which entails limiting data access. The Zero Trust security approach...
AttackCrypt, an open-source “crypter,” was recently used by cybercriminals to hide malware binaries and avoid antivirus detection. A crypter is a kind of software that can...
DETROIT (AP) — A 46% pay raise. A 32-hour week with 40 hours of pay. A restoration of traditional pensions. The demands that a...
BLACK ROCK DESERT, Nev. (AP) — Tens of thousands of partygoers were still stranded Monday morning in the northern Nevada desert after a late-summer...
STOCKHOLM (AP) — Clashes erupted in an immigrant neighborhood in Sweden’s third largest city after an anti-Muslim protester set fire to a copy of...