Azure Active Directory (AAD) has a new attack vector that affected Microsoft’s Bing.com, according to Wiz Research. A widespread AAD misconfiguration is the attack vector, making misconfigured apps vulnerable to intrusion.
Microsoft’s AAD, a cloud-based identity and access management (IAM) service, is the standard authentication method for Azure App Services and Azure Functions applications.
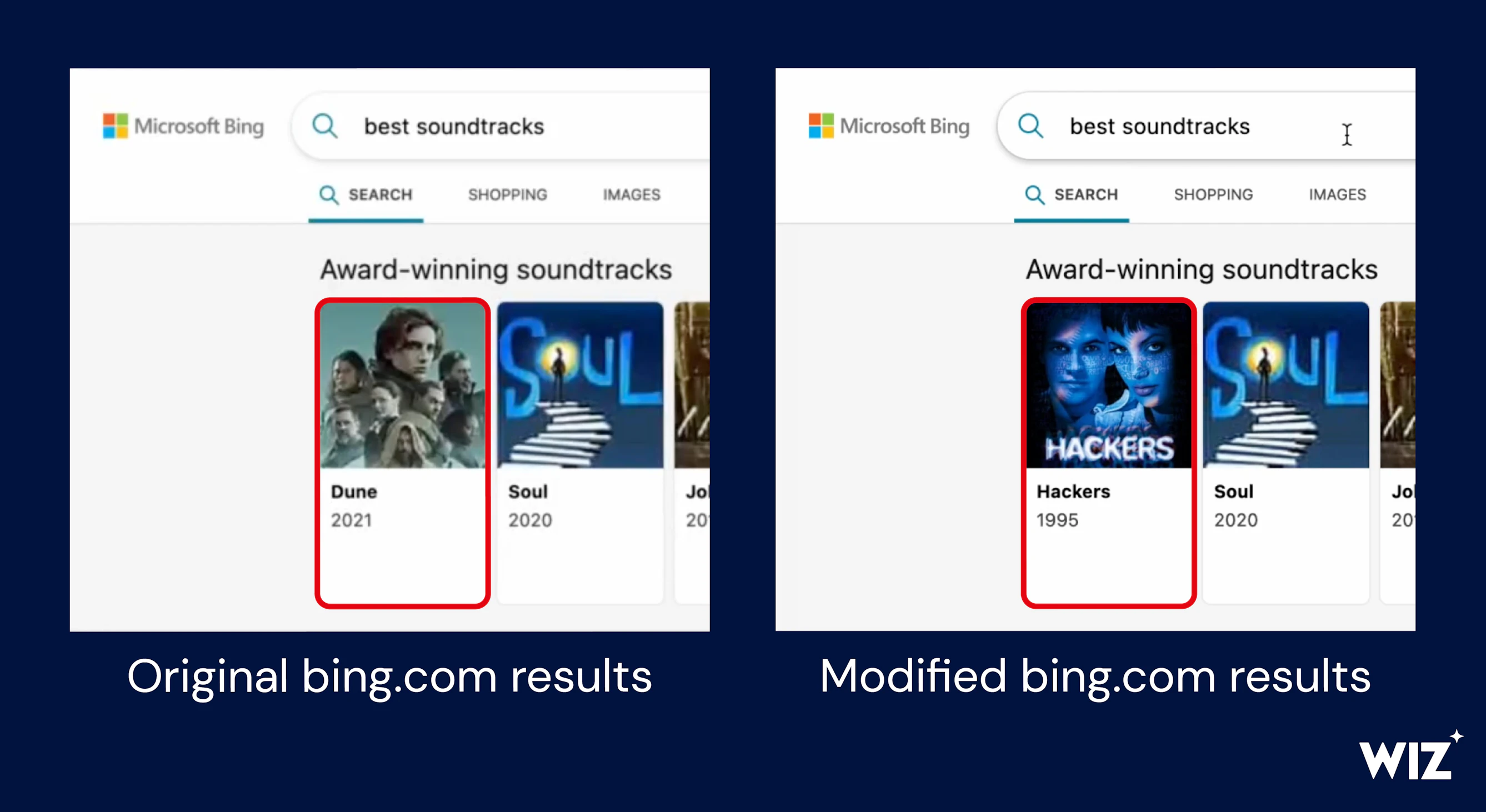
“The researchers found several Microsoft applications vulnerable to this attack, one of which was a Content Management System (CMS) that powers Bing.com,” says Wiz researchers.“This allowed them to take over Bing.com functionality, modify search results, and potentially enable the Office 365 credential theft of millions of Bing users. These credentials in turn granted access to users’ private emails and documents”.
Unsafe Configuration Found in AAD
In general, single-tenant, multi-tenant, personal accounts, or a combination of the last two are the various account access options AAD offers.
Any user from any Azure tenant may log in to a multi-tenant app. The developer must verify the user’s original tenant in a multi-tenant app and give access appropriately. Anyone with an Azure account from anywhere worldwide could access the app if they fail to validate this information properly.
Researchers say developers may not always understand this Shared Responsibility architecture, so setup and validation errors are frequently made.
Almost 25% of the multi-tenant apps researchers analyzed during the investigation were obvious weaknesses.”Bing Trivia,” a Microsoft-produced app, was on the list.
The researchers could access this app with their Azure user because it was misconfigured. They then discovered a Content Management System (CMS) connected to Bing.com.
“A malicious actor landing on the Bing Trivia app page could therefore have tampered with any search term and launched misinformation campaigns, as well as phished and impersonated other websites,” Wiz researchers explain.
The researchers learned that Bing and Office 365 were linked and could add cross-site scripting (XSS) payload into Bing.com, allowing them to compromise any user’s Office 365 token.
“With a stolen token, a potential attacker could access Bing users’ Office 365 data, including Outlook emails, calendars, Teams messages, SharePoint documents, and OneDrive files”, researchers.
So, a bad actor with the same access might have used the most popular search results to hijack them with the same payload and leak millions of users’ sensitive information.
Recommendation
Mag News, Centralized Notification Service (CNS) API, Contact Center, PoliCheck, Power Automate Blog, and the file management system COSMOS were also among the internal Microsoft applications harmed by the misconfiguration.
Administrators are encouraged to double-check their applications’ configurations to ensure that multi-tenant access is set up correctly or to switch to single-tenant authentication if multi-tenancy is unnecessary.
It’s also advised to look through logs for the previous activity for susceptible applications (AAD logs, however, are insufficient for that).
Microsoft quickly patched its susceptible apps and changed the functioning of several AAD features to minimize customer exposure. Whiz reported the initial Bing bug on January 31, and Microsoft rectified it that day. The tech giant awarded a bug bounty of $40,000.
Copyright 2021 Associated Press. All rights reserved.








































