Threat analysts at AquaSec have spotted signs of TeamTNT activity on their honeypots since early September, leading them to believe the notorious hacking group is back in action.
TeamTNT announced it was quitting back in November 2021, and indeed, most associated observations since then involved remnants of past infections like automated scripts but no new payloads.
However, the recent attacks bear various signatures linked to TeamTNT and rely on tools previously deployed by the gang, indicating that the threat actor is likely making a comeback.
Targeting Bitcoin encryption
The researchers observed three attack types being used in the allegedly new TeamTNT attacks, with the most interesting one being to use the computational power of hijacked servers to run Bitcoin encryption solvers.
Named “the Kangaroo attack,” due to using Pollard’s Kangaroo WIF solver, the attack scans for vulnerable Docker Daemons, deploys an AlpineOS image, drops a script (“k.sh”), and eventually fetches the solver from GitHub.
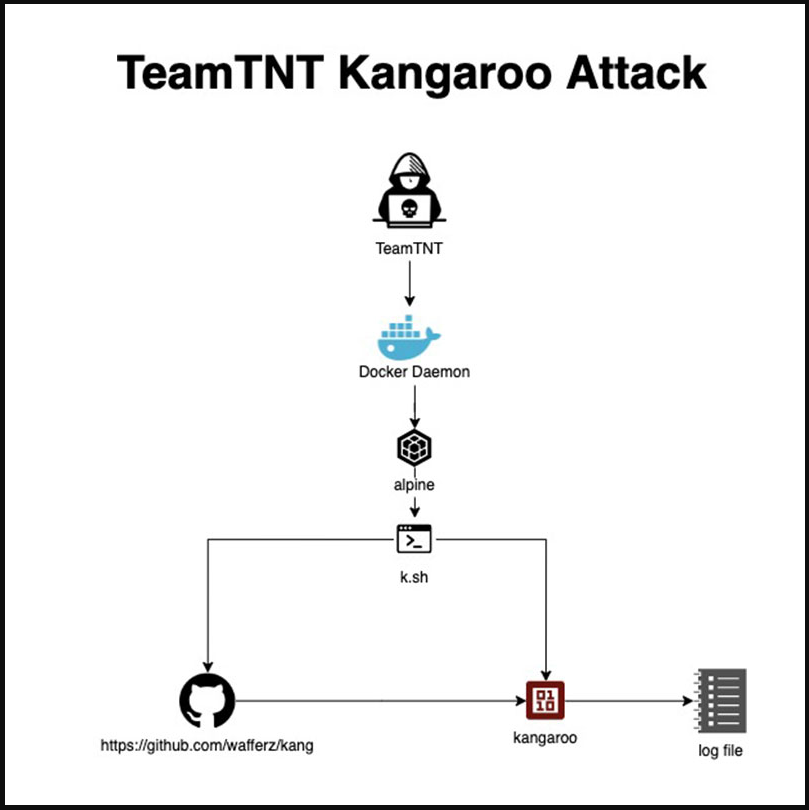
Pollard’s Kangaroo interval ECDLP (Elliptic Curve Discrete Logarithm Problem) solver algorithm is an attempt to break SECP256K1 encryption used in Bitcoin’s public-key cryptography.
“It [the algorithm] is designed to run in a distributed fashion since the algorithm breaks the key into chunks and distributes them to various nodes (attacked servers), collecting the results which are then written locally to a text file,” explains AquaSec.
While quantum computing is expected to break existing Bitcoin encryption at some point in the future, it’s considered impossible to achieve it with current machines, but TeamTNT appears willing to try out the theory anyway using other people’s resources.
Possibly, the threat actors are merely experimenting with new attack pathways, payload deployment, and evading detection while performing intensive operations on captured systems, with the Kangaroo attack ticking all boxes.
Other attack types
The other attacks observed by AquaSec are similar to past TeamTNT operations but now feature some novel characteristics.
The “Cronb Attack” uses documented rootkits, cron jobs for persistence, cryptominers for profit, and tools for lateral movement. The novel element is the appearance of new C2 infrastructure addresses and more elaborate data exchange.
The “What Will Be” attack targets Docker Daemons with shell-file dropping Alpine images again, exploiting a vulnerability to escape from the container to the host.
Next, the intruders download and execute additional scripts, rootkits, and a cryptominer, while they also add cronjobs and perform SSH scans on the network.
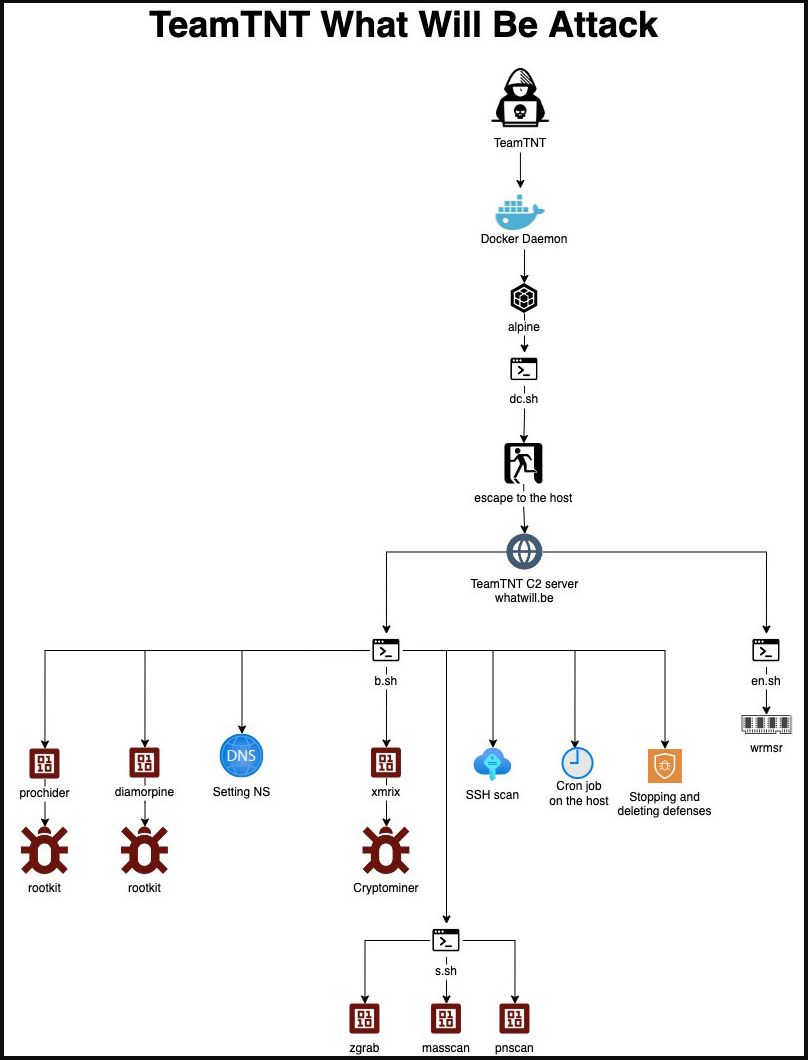
One new trick in this attack is introduced via those scripts, enabling the threat actors to optimize cryptomining performance by modifying CPU model-specific registers for the architecture.
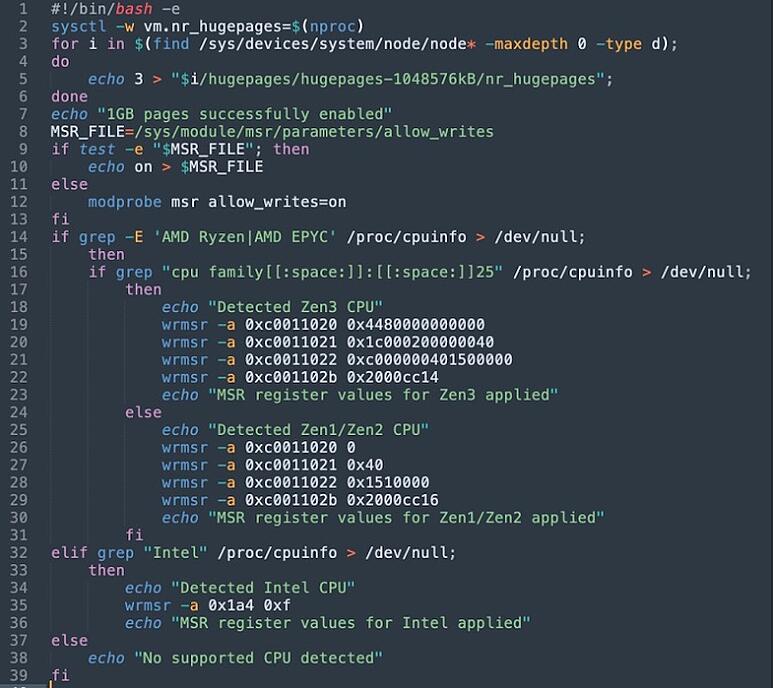
Whether it is TeamTNT conducting these attacks or someone else, organizations should ramp up their cloud security, strengthen Docker configuration, and apply all available security updates before it’s too late.