The threat actor behind BRATA banking trojan has evolved their tactics and improved the malware with information-stealing capabilities.
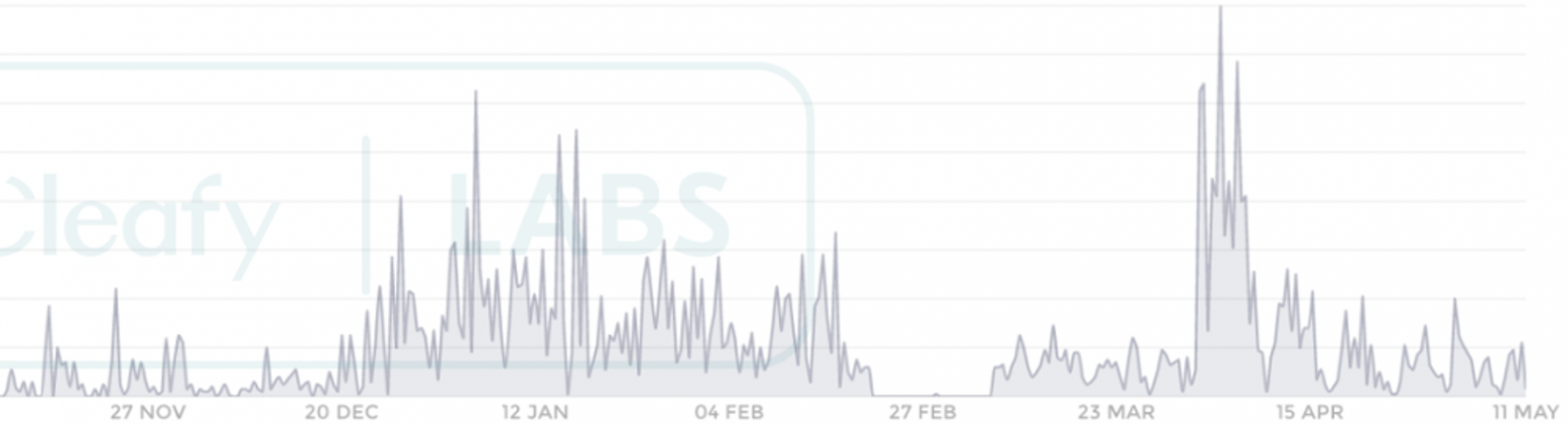
Italian mobile security company Cleafy has been tracking BRATA activity and noticed in the most recent campaigns changes that lead to longer persistence on the device.
“The modus operandi now fits into an Advanced Persistent Threat (APT) activity pattern,” explains Cleafy in a report this week.
“This term is used to describe an attack campaign in which criminals establish a long-term presence on a targeted network to steal sensitive information.”
The malware itself has also been updated with new phishing techniques, new classes to request additional permissions on the device, and now also drops a second-stage payload from the command and control (C2) server.
Targeted campaigns
BRATA malware is also more targeted, as the researchers discovered that it focuses on one financial institution at a time and only pivot to a different one when their attacks are rendered inefficient by countermeasures.
For example, BRATA now comes pre-loaded with a single phishing overlay instead of acquiring a list of installed apps and fetching the right injections from the C2.
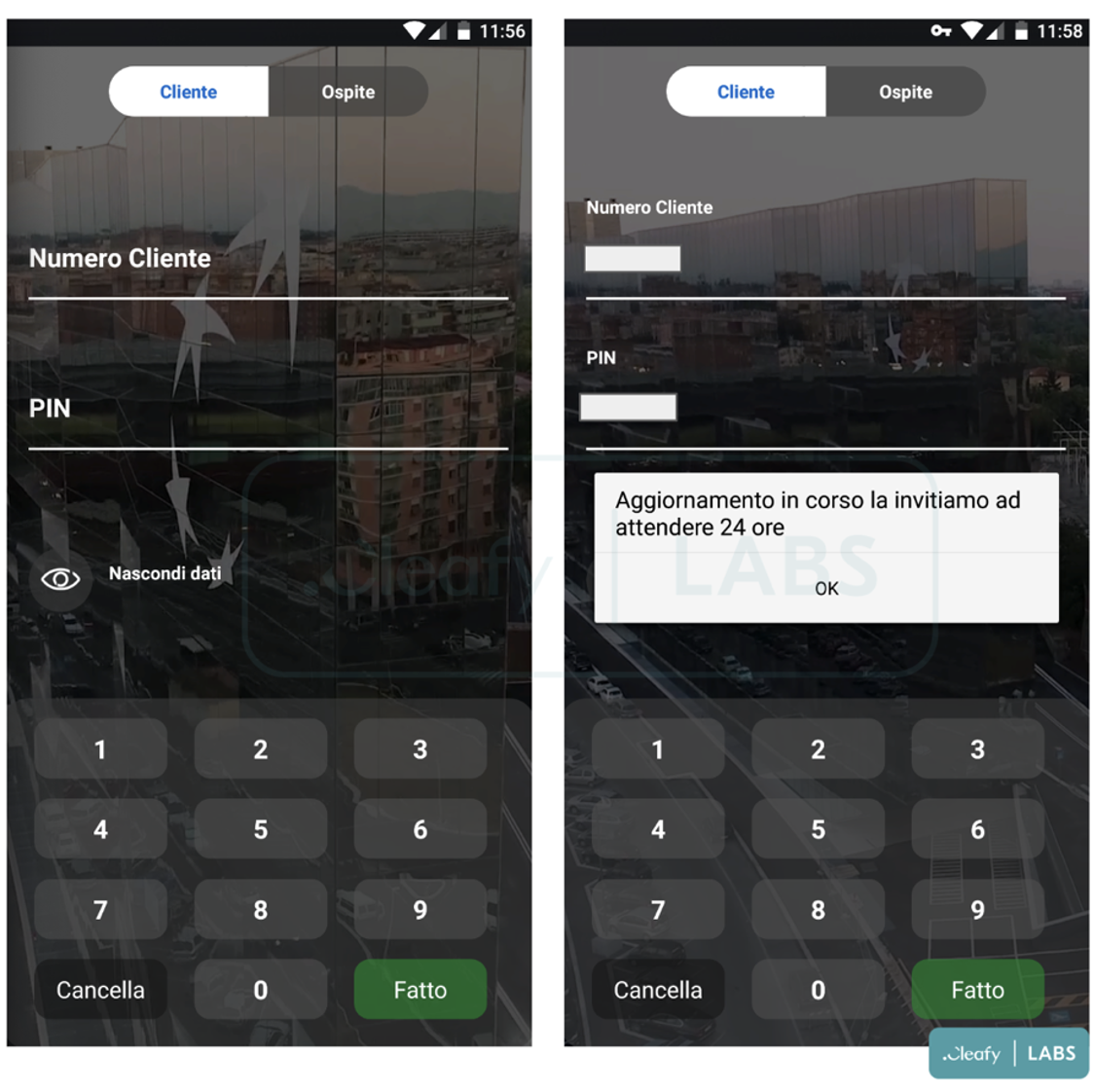
This minimizes the malicious network traffic and the interactions with the host device.
In a more recent version, BRATA adds more permissions that allow it to send and receive SMS, which can help attackers steal temporary codes like one-time passwords (OTPs) and two-factor authentication (2FA) that banks send to their customers.
After nesting into a device, BRATA fetches a ZIP archive from the C2 server containing a JAR (“unrar.jar”) package.
This keylogging utility monitors app-generated events and stores them locally on the device with the text data and a matching timestamp.
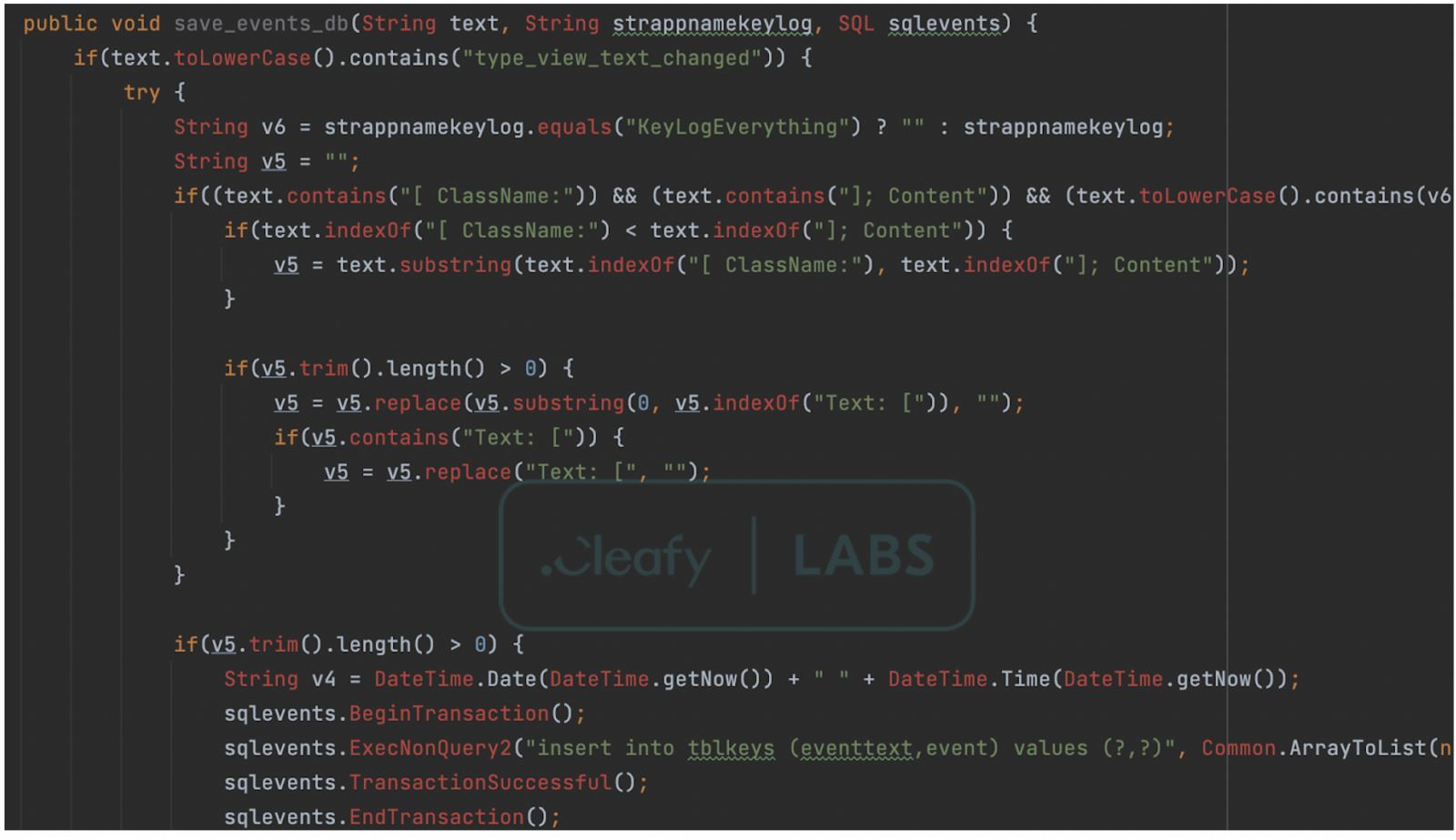
Cleafy’s analysts saw signs that this tool is still in early development and the researchers think that the author’s ultimate goal is to abuse the Accessibility Service to get data from other applications.
The BRATA evolution
BRATA started as a banking trojan in Brazil in 2019, able to perform screen capturing, install new apps, and turn off the screen to make the device appear powered down.
In June 2021, BRATA made its first appearance in Europe, using fake anti-spam apps as a lure and employing fake support agents who defrauded victims and tricked them into giving them complete control of their devices.
In January 2022, a new version of BRATA emerged in the wild, using GPS tracking, multiple C2 communication channels, and tailored versions for banking customers in different countries. That version also featured a factory reset command that wiped devices after all data had been stolen.
Now, besides the new BRATA version and the change in tactics, Cleafy has also found a new project: an SMS stealer app that communicates with the same C2 infrastructure.
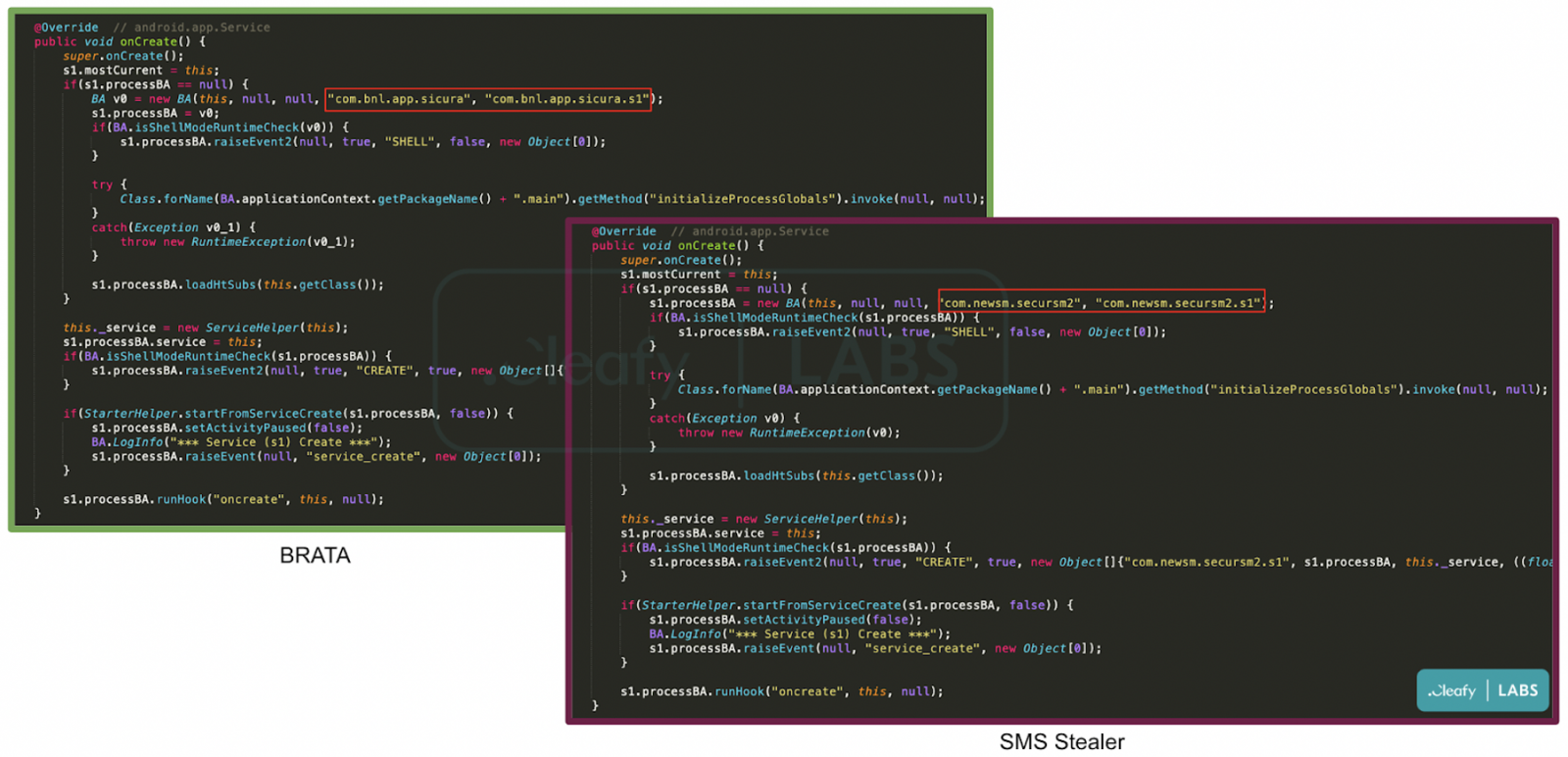
It uses the same framework as BRATA and the same class names, but it seems to be focused only on syphoning short text messages. Currently, it targets the UK, Italy, and Spain.
To intercept incoming SMS, the application asks the user to set it as the default messaging app while also requesting permission to access contacts on the device.
.png)
For now, it’s unclear if this is just an experiment on an effort of the BRATA team to create simpler apps devoted to specific roles.
What is clear is that BRATA keeps evolving with a cadence of about two months. It’s imperative to stay vigilant, keep your device up to date, and avoid installing apps from unofficial or suspicious sources.










































