A new and destructive ‘Azov Ransomware’ data wiper is being heavily distributed through pirated software, key generators, and adware bundles, trying to frame well-known security researchers by claiming they are behind the attack.
The Azov Ransomware falsely claims to have been created by a well-known security researcher named Hasherazade and lists other researchers, myself, and BleepingComputer, as involved in the operation.
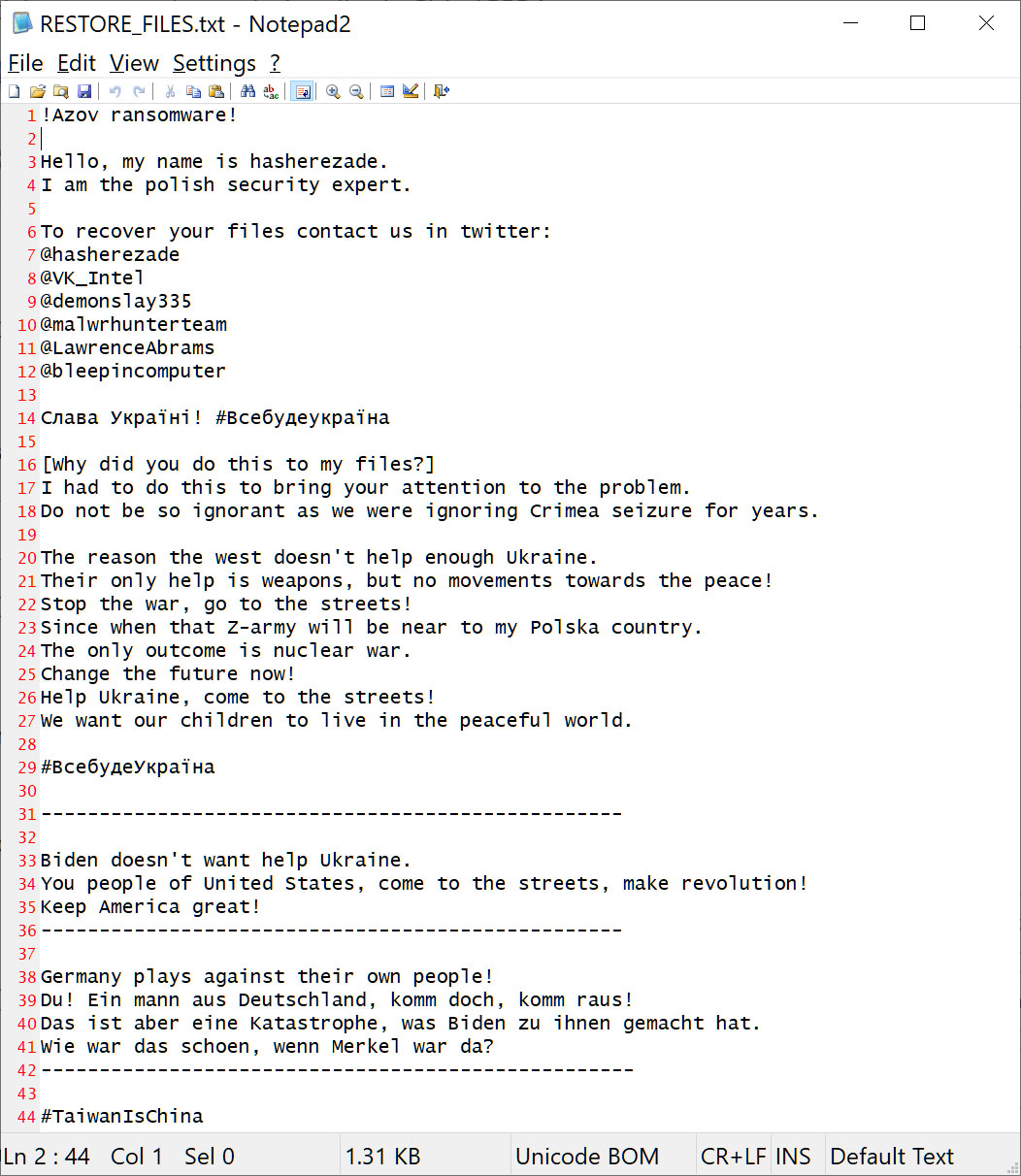
The ransom note, named RESTORE_FILES.txt, says that devices are encrypted in protest of the seizure of Crimea and because Western countries are not doing enough to help Ukraine in their war against Russia.
Source: BleepingComputer
The ransom note tells victims to contact me, BleepingComputer, Hasherazade, MalwareHunterTeam, Michael Gillespie, or Vitali Kremez on Twitter to recover files, falsely implying that we are part of the ransomware operation.
To be clear, those listed in the ransom note are not associated with this ransomware and are being framed by the threat actor. Therefore, we, unfortunately, do not have the decryption keys and cannot help.
Furthermore, as there is no way to contact the threat actors to pay a ransom, this malware should be treated as a destructive data wiper rather than ransomware.
Unfortunately, victims have already started contacting BleepingComputer for help recovering files, and as much as we would like to help, there is no known way of helping at this time.
While the threat actors claim they are doing this in support of Ukraine, BleepingComputer knows of a Ukrainian organization affected by this data wiper.
The wiper takes its name from the Ukrainian Azov Regiment, a controversial military force that allegedly associated with neo-Nazi ideology in the past.
This is not the first time threat actors attempted to frame security researchers for their malware.
In 2016, the Apocalypse ransomware operation renamed one of its variants to Fabiansomware after Fabian Wosar. In 2020, one of the Maze ransomware developers released an MBR Locker, claiming it was made by Vital Kremez.
What we know about the Azov wiper
In a new campaign started over the past two days, a threat actor appears to have purchased ‘installs’ through the SmokeLoader malware botnet to deliver the new destructive Azov wiper.
SmokeLoader is a malware botnet that other threat actors can rent or buy ‘installs,’ to distribute their own malware on infected devices. SmokeLoader is commonly distributed through websites pushing fake software cracks, game modifications, cheats, and key generators.
Over the past few days, SmokeLoader has begun delivering the new ‘Azov Ransomware,’ along with other malware [VirusTotal], such as the RedLine Stealer information-stealing malware and the STOP ransomware.
BleepingComputer is aware of victims being double-encrypted, first with Azov and then with STOP ransomware, as SmokeLoader delivered both simultaneously.
The initial ransomware executable [VirusTotal] will be dropped under a random file in the Windows temp (%Temp%) folder and executed.
Once launched, the wiper will copy C:\Windows\System32\msiexec.exe to C:\ProgramData\rdpclient.exe [VirusTotal] and patch it to also contain the Azov wiper. Additionally, the wiper may be configured to launch when Windows starts using the following Registry key.
[HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\]
“Bandera” = “C:\ProgramData\rdpclient.exe”
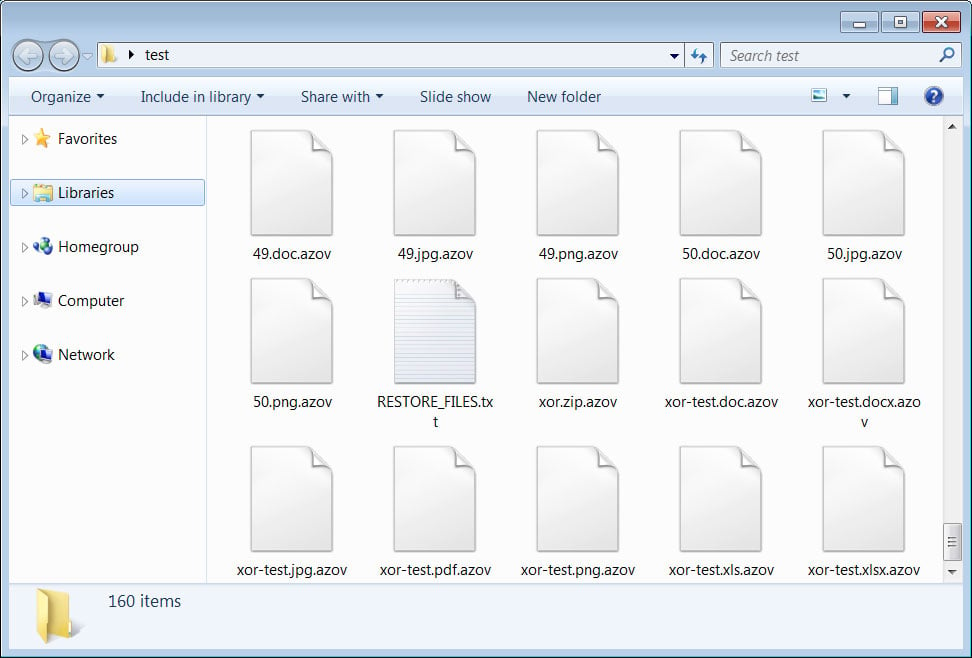
The wiper will now scan all the drives on the computer and encrypt any file that does not have the .ini, .dll, and .exe extensions.
When encrypting files, it will append the .azov file extension to the names of encrypted files. For example, 1.doc is encrypted and renamed to 1.doc.azov, as shown below.
Source: BleepingComputer
In each folder that is scanned for files, the wiper will create text files named RESTORE_FILES.txt that contain a message from the threat actor, as shown previously in the article.
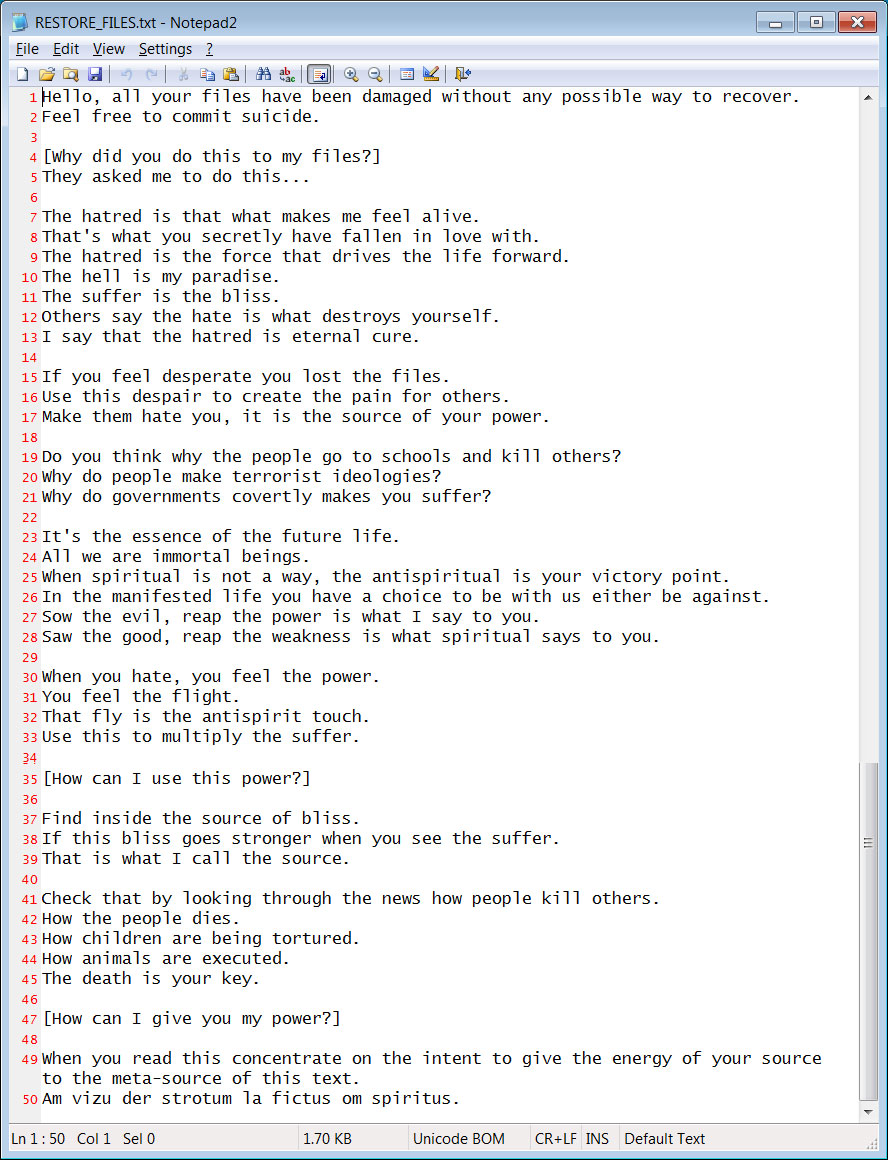
A previous version of the wiper found by MalwareHunterTeam used a different ransom note with a much darker message.
Source: BleepingComputer
While the ransomware will be analyzed by researchers for weaknesses in the encryption, at this time, the ransomware should be considered destructive, as there is no way to contact the threat actors and recover decryption keys.
We will update this article if a method is discovered to recover files for free.
However, if this data wiper encrypted your data, you were likely also infected with other malware, such as information-stealing trojans.
Therefore, you should immediately change the passwords on your online accounts, especially those sensitive in nature, such as online banking, password managers, and email accounts.
Copyright 2021 Associated Press. All rights reserved.










































