A free unofficial patch has been released for an actively exploited zero-day that allows files signed with malformed signatures to bypass Mark-of-the-Web security warnings in Windows 10 and Windows 11.
Last weekend, BleepingComputer reported that threat actors were using stand-alone JavaScript files to install the Magniber ransomware on victims’ devices.
When a user downloads a file from the Internet, Microsoft adds a Mark-of-the-Web flag to the file, causing the operating system to display security warnings when the file is launched, as shown below.
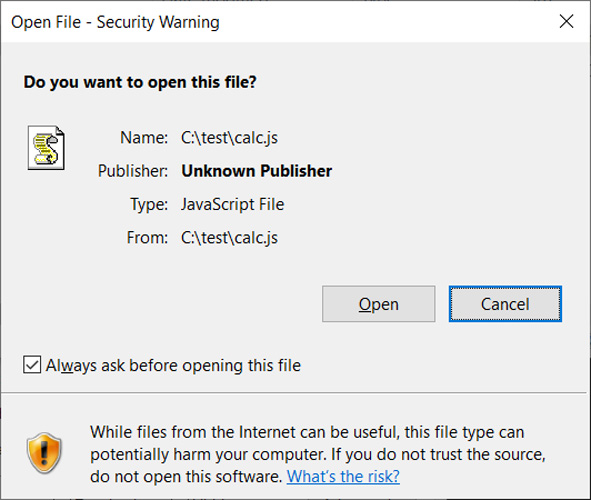
Source: BleepingComputer
What made these Magniber JavaScript files stand out was that even though they contained a Mark-of-a-Web, Windows did not display any security warnings when they were launched.
After being analyzed by Will Dormann, a senior vulnerability analyst at ANALYGENCE, he discovered that the JavaScript files were digitally signed using a malformed signature.
When a malicious file with one of these malformed signatures is opened, instead of being flagged by Microsoft SmartScreen and showing a security warning, Windows would automatically allow the program to run.
The image below demonstrates how the vulnerability allows a file (‘calc-othersig.js’) with a malformed signature to bypass the Mark-of-the-Web security warning.
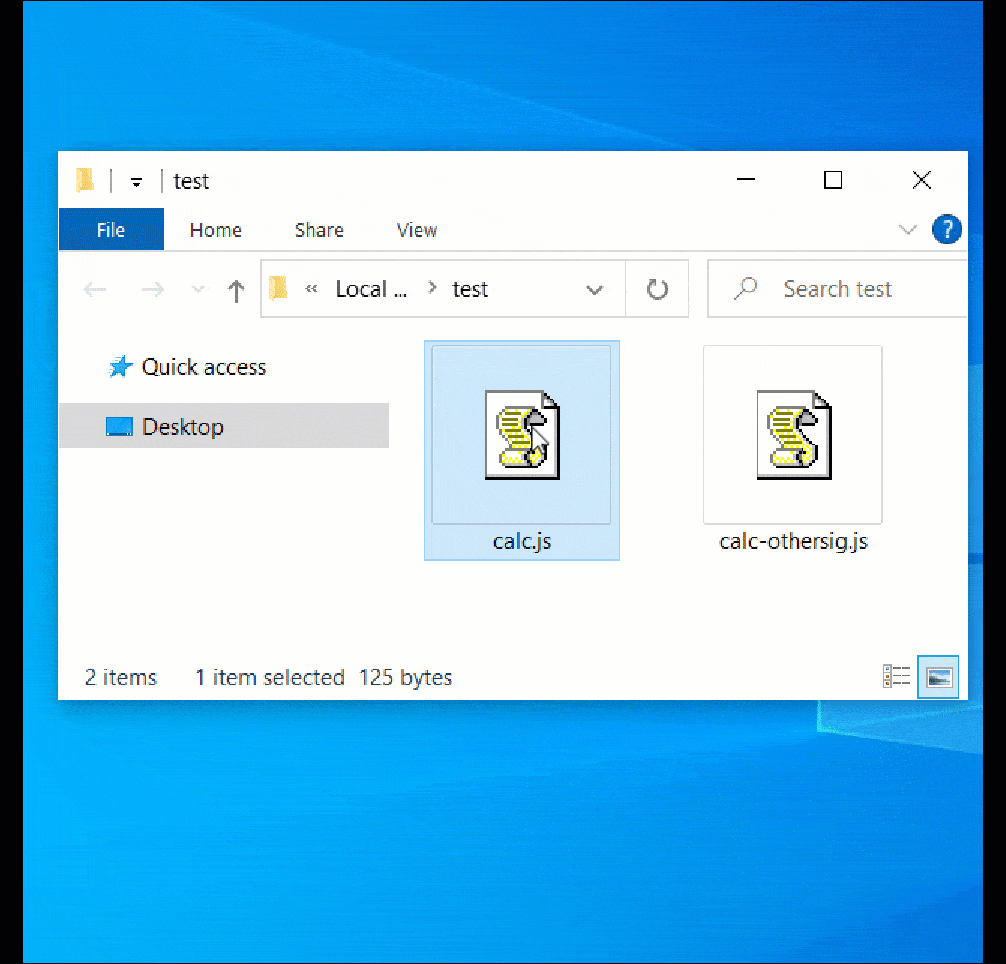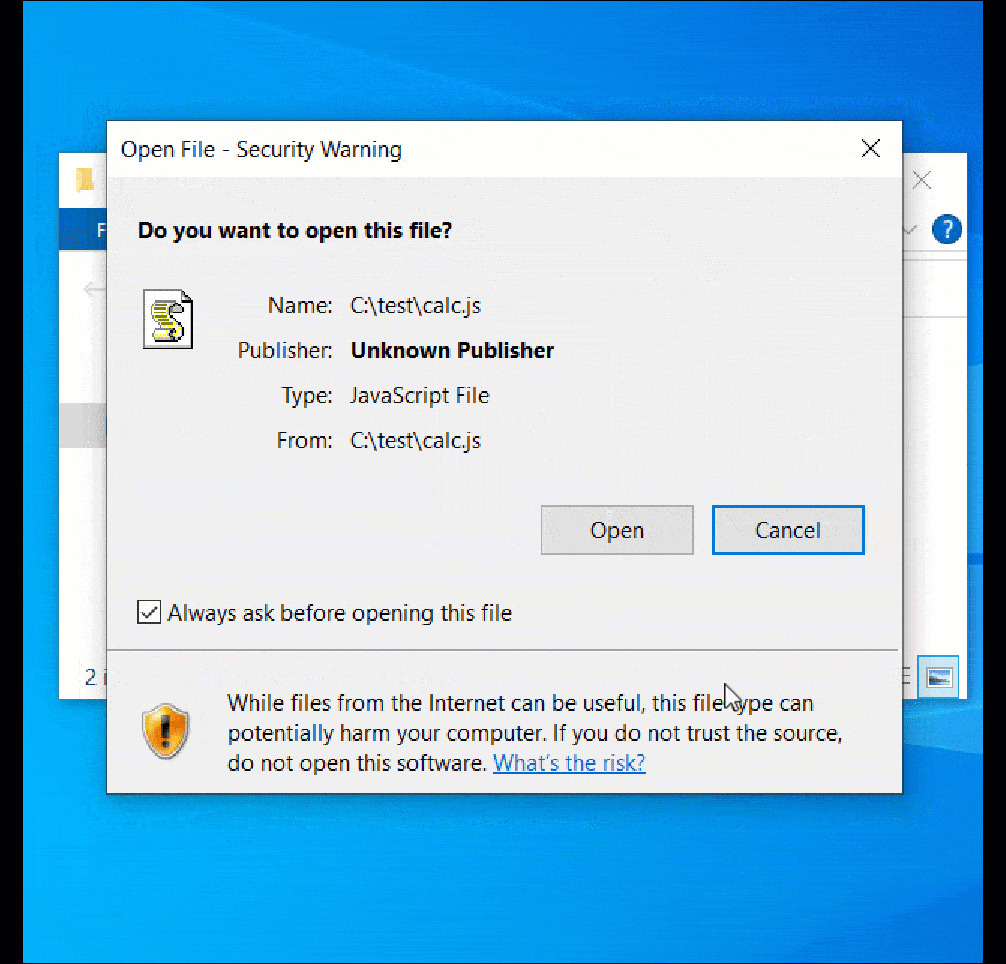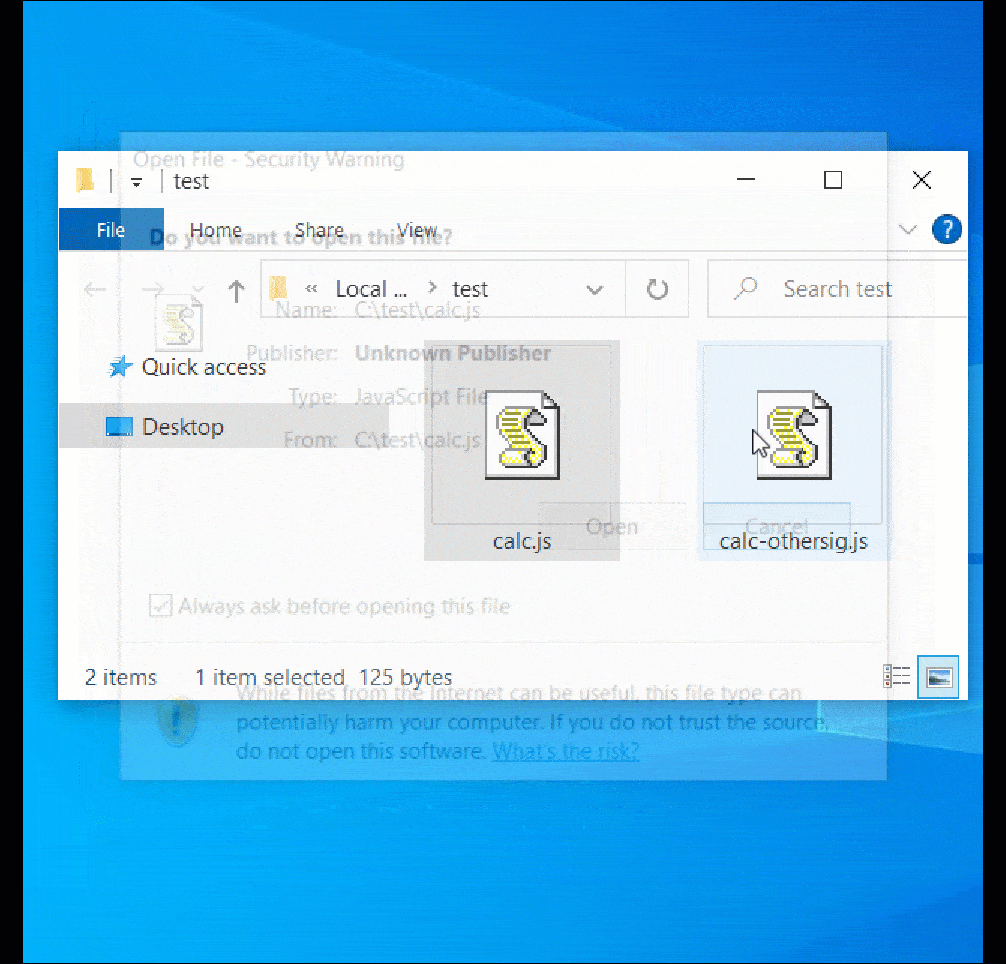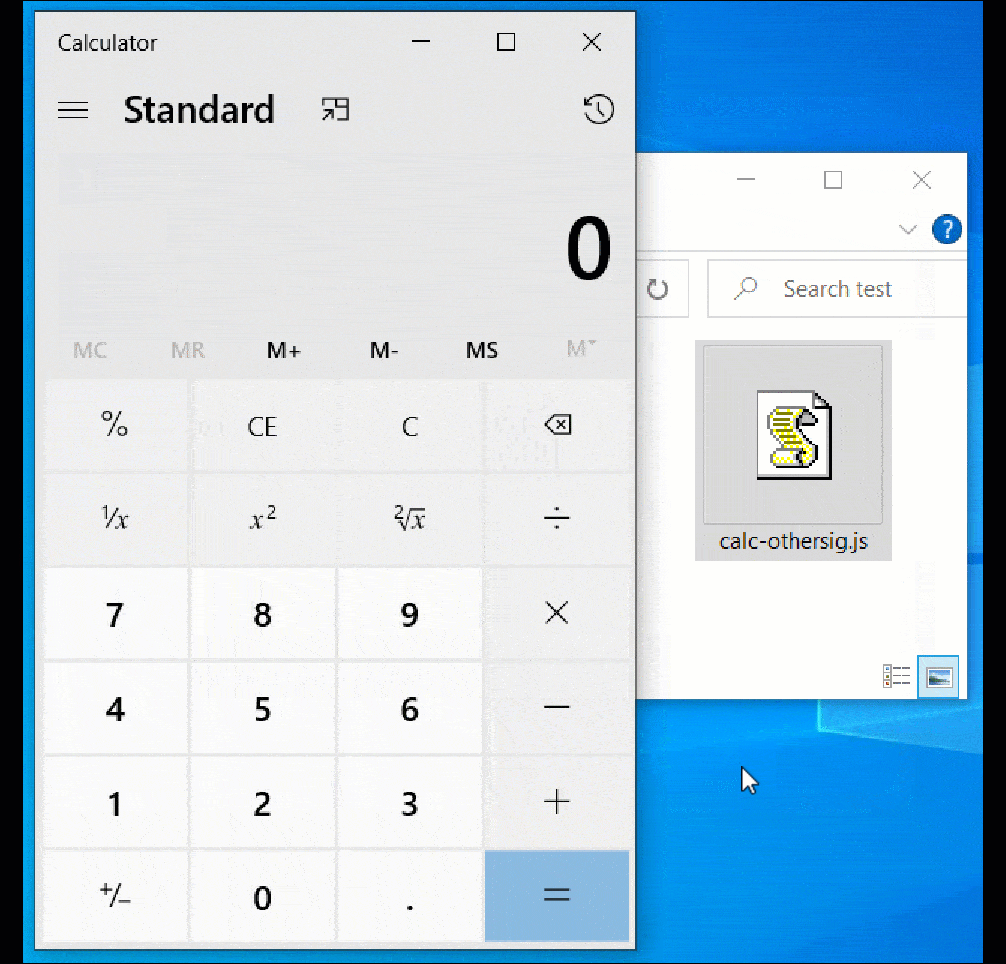
Source: BleepingComputer
Microsoft told BleepingComputer that they were aware of the issue and investigating it.
Free unofficial patch released
As this zero-day vulnerability is actively exploited in ransomware attacks, the 0patch micro-patching service decided to release an unofficial fix that can be used until Microsoft releases an official security update.
In a 0patch blog post, co-founder Mitja Kolsek explains that this bug is caused by Windows SmartScreen’s inability to parse the malformed signature in a file.
When SmartScreen can’t parse the signature, Windows will incorrectly allow the program to run rather than displaying an error.
“The malformed signature discovered by Patrick and Will caused SmartScreen.exe to throw an exception when the signature could not be parsed, resulting in SmartScreen returning an error,” explains Kolsek.
“Which we now know means “Run”.”
Kolsek warned that though their patch fixes the majority of attack scenarios, there could also be situations that bypass his patch.
“While our patch fixes the most obvious flaw, its utility depends on the application opening the file using function DoSafeOpenPromptForShellExe in shdocvw.dll and not some other mechanism,” warns Kolsek.
“We’re not aware of another such mechanism in Windows, but it could technically exist.”
Until Microsoft releases official updates to address the flaw, 0patch has developed free patches for the following affected Windows versions:
- Windows 11 v21H2
- Windows 10 v21H2
- Windows 10 v21H1
- Windows 10 v20H2
- Windows 10 v2004
- Windows 10 v1909
- Windows 10 v1903
- Windows 10 v1809
- Windows 10 v1803
- Windows Server 2022
- Windows Server 2019
To install the micropatch on your Windows device, you will need to register a free 0patch account and install its agent.
Once the agent is installed, the patches will be applied automatically without requiring a system restart if there are no custom patching policies to block it.
You can see 0patch’s Windows micropatches in action in the video below.
Copyright 2021 Associated Press. All rights reserved.










































