A new malware dropper named ‘NullMixer’ is infecting Windows devices with a dozen different malware families simultaneously through fake software cracks promoted on malicious sites in Google Search results.
NullMixer acts as an infection funnel, using a single Windows executable to launch a dozen different malware families, leading to over two dozen infections running a single device.
These infections range from password-stealing trojans, backdoors, spyware, bankers, fake Windows system cleaners, clipboard hijackers, cryptocurrency miners, and even further malware loaders.
To distribute the malware, the malware distributors use ‘black hat SEO’ to display websites promoting the fake game cracks and pirated software activators in high search result positions on Google.
BleepingComputer tested a Google search for ‘software crack,’ and many of the sites said to be distributing this malware, as shown below, were listed in our search results in the second, third, and fourth search result positions.
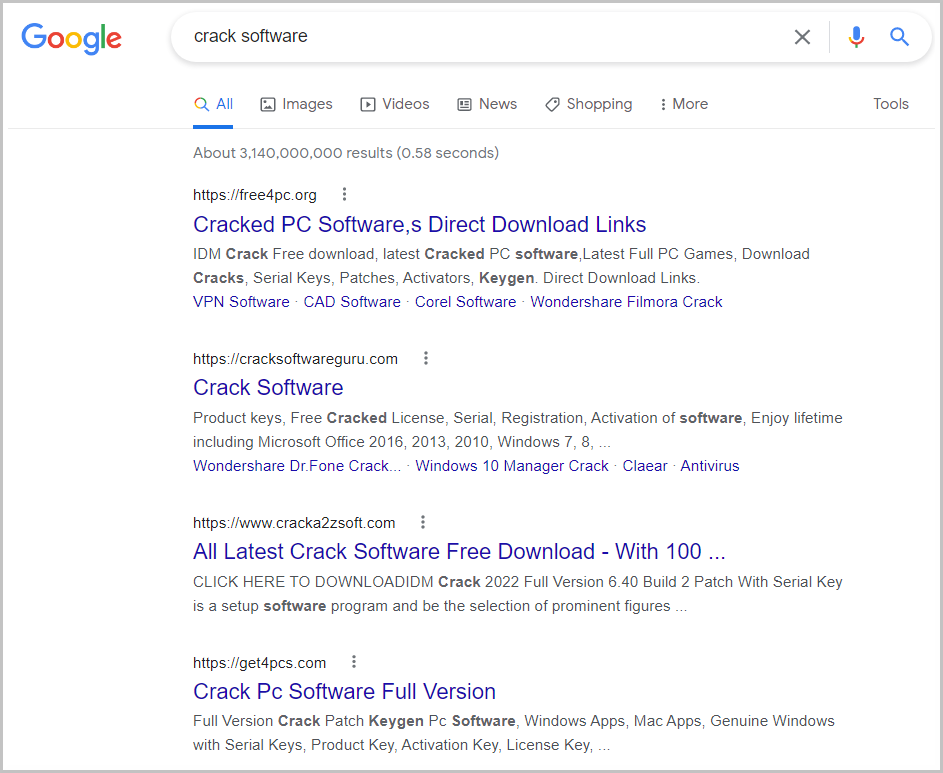
Unsuspecting users who attempt to download software from these sites are redirected to other malicious sites that drop a password-protected ZIP archive containing a copy of the NullMixer dropper.
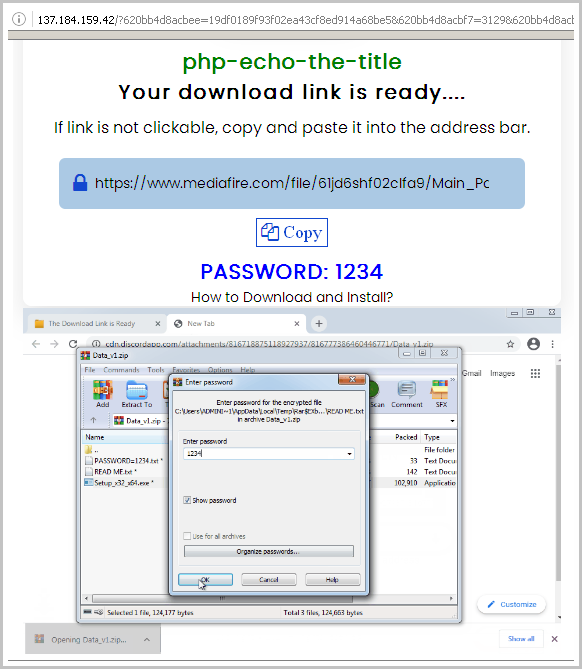
Because software cracks and cheats commonly need to modify game files, users downloading them disregard AV warnings about unsigned and potentially dangerous executables, bypassing security controls and executing them manually.
Kaspersky, whose analysts discovered the new dropper, reports that NullMixer has already attempted infections on 47,778 of its customers across the United States, Germany, France, Italy, India, Russia, Brazil, Turkey, and Egypt.
Launching dozens of malware
NullMixer is commonly downloaded as files named similarly to ‘win-setup-i864.exe,’ that when launched, create a new file called ‘setup_installer.exe.’
This new file is responsible for dropping dozens of malware families and, having done that, launches another executable, ‘setup_install.exe.’
That third file launches all malware dropped in the compromised machine using a hardcoded list of their names and the Windows’ cmd.exe’ tool.
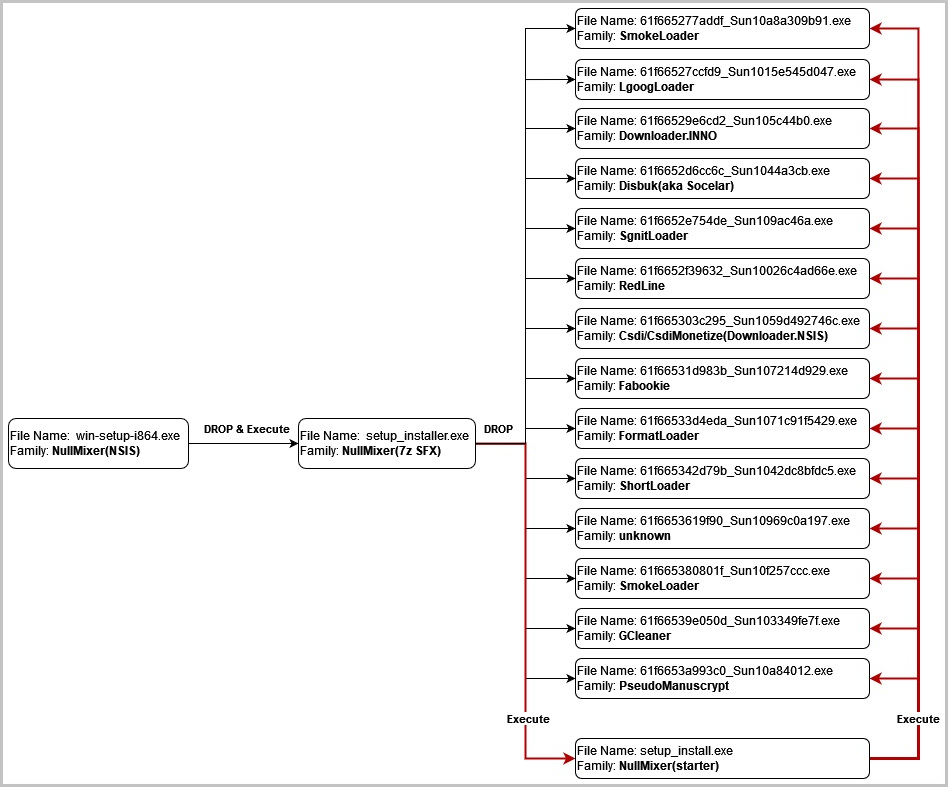
Some malware families dropped by NullMixer include Redline Stealer, Danabot, Raccoon Stealer, Vidar Stealer, SmokeLoader, PrivateLoader, ColdStealer, Fabookie, PseudoManuscrypt, and more.
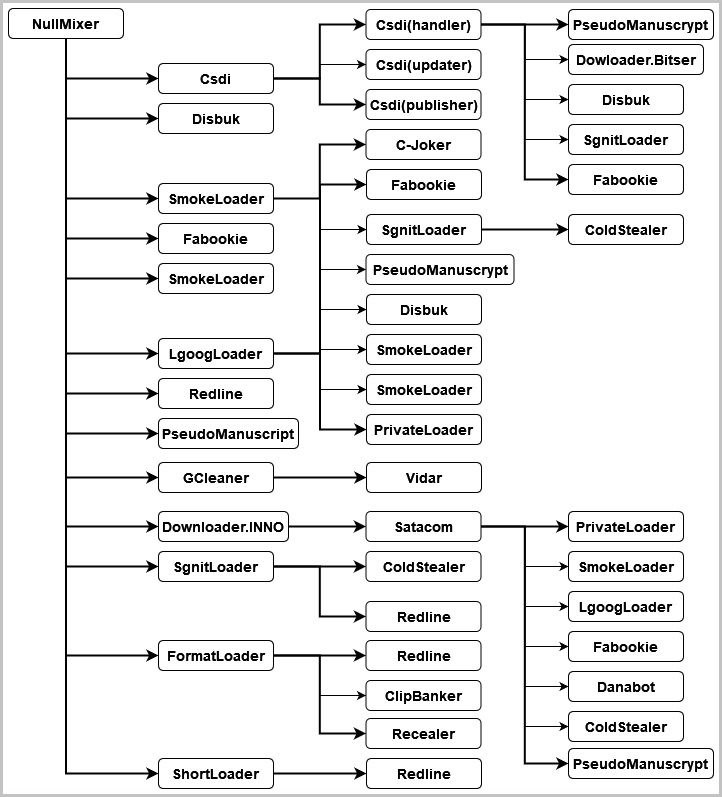
The reason why NullMixer operators chose to install and launch all these malware families simultaneously on randomly compromised computers is unclear.
The operators may opt to cause destruction for fame, promote their tool as a very effective dropper to malware gangs, or achieve absurd levels of redundancy.
Whatever the case, it would be practically impossible for all those malware families to run on a breached computer and not generate abundant symptoms of compromise for the victim to realize the infection.
These symptoms could include heavy hard disk activity, increased CPU and memory utilization, unusual windows opening for no reason, or simply a noticeable performance issue on the infected device.
Thus, NullMixer is less of a stealthy threat now and more of a catastrophic encounter that can likely only be resolved through a reinstall of Windows.
Users must always consider the risks of downloading executables from obscure online sources and avoid resorting to software piracy.










































