While monitoring the Emotet botnet’s current activity, security researchers found that the Quantum and BlackCat ransomware gangs are now using the malware to deploy their payloads.
This is an interesting development given that the Conti cybercrime syndicate was the one that previously used the botnet before shutting down in June.
The Conti group was the one who orchestrated its comeback in November after an international law enforcement action took down Emotet’s infrastructure at the beginning of 2021.
“The Emotet botnet (also known as SpmTools) has fueled major cybercriminal groups as an initial attack vector, or precursor, for numerous ongoing attacks,” security researchers at intelligence company AdvIntel said.
“From November 2021 to Conti’s dissolution in June 2022, Emotet was an exclusive Conti ransomware tool, however, the Emotet infection chain is currently attributed to Quantum and BlackCat.”
The botnet is now being used to install a Cobalt Strike beacon on infected systems as a second-stage payload, according to AdvIntel, allowing attackers to move laterally and deploy ransomware payloads across the victim’s network.
This matches Conti’s attack flow that included Emotet after its revival, minus the initial access vector through the TrickBot botnet.
AdvIntel says that Emotet has been inflicting quite a lot of damage since the start of the year as it has tracked more than 1,200,000 systems infected by Emotet worldwide, with an activity peak between February and March.
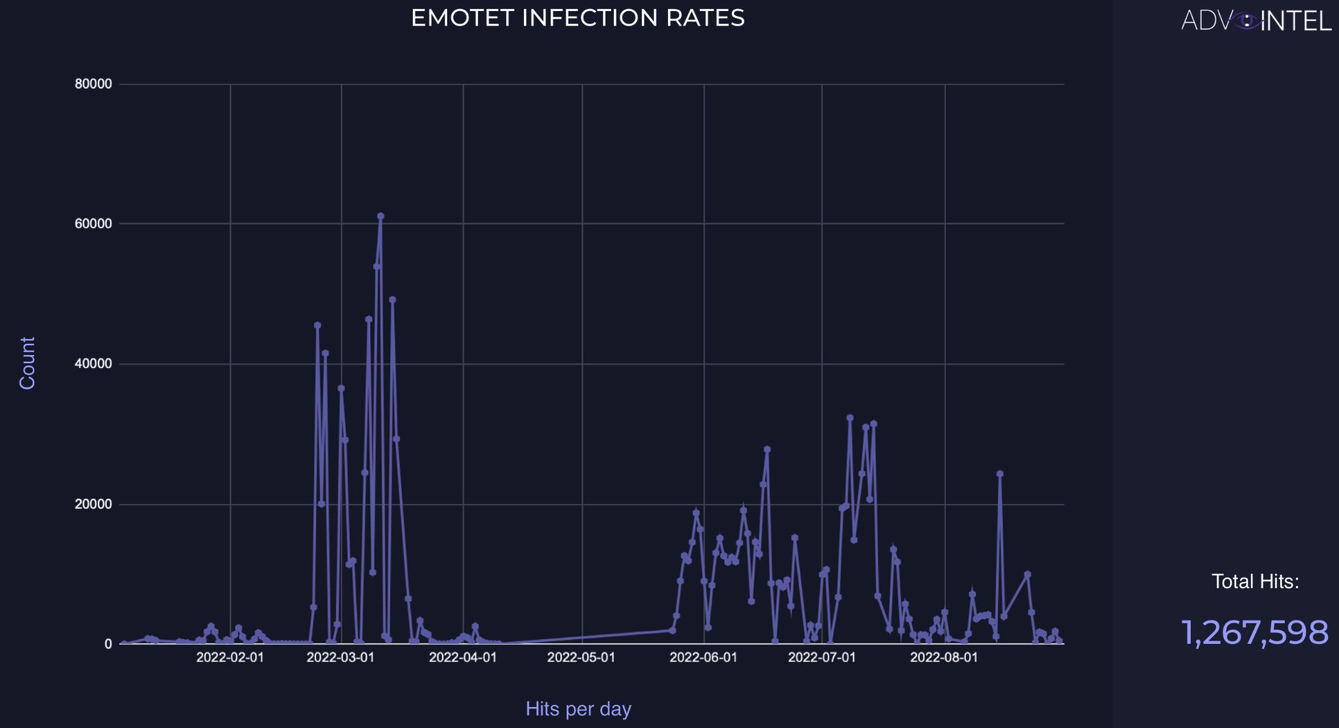
AdvIntel’s assessment was confirmed in June by ESET who said it detected a massive increase in Emotet activity since the start of the year, “growing more than 100-fold vs T3 2021.”
Agari also revealed in August that the botnet saw a significant surge in Q2, replacing QBot in phishing campaigns, collectively accounting for more than 90% of all malware that landed in its customers’ inboxes.
The Emotet malware was first deployed in attacks as a banking trojan in 2014 and has evolved into a botnet used by the TA542 threat group (aka Mummy Spider) to steal data, perform reconnaissance, and move laterally throughout victims’ networks, as well as to deliver second-stage malicious payloads.
Since June, the botnet was upgraded to infect potential victims with a credit card stealer module that will attempt to harvest credit card information stored in Google Chrome user profiles.
This change came after increasing activity during April and a switch to 64-bit modules, as the Cryptolaemus security research group spotted.
Emotet (just like Qbot and IcedID) has also switched to Windows shortcut files (.LNK) from using Microsoft Office macros (now disabled by default) as an attack vector to infect targets’ devices.
Thankfully, Emotet campaigns are not very active, if at all, right now, with most malware phishing campaigns revolving around Qbot and IcedID.
However, that could quickly change and lead to rapid deployment of ransomware attacks, so Emotet continues to be a malware defenders have to look out for.










































