A set of six high-severity firmware vulnerabilities impacting a broad range of HP devices used in enterprise environments are still waiting to be patched, although some of them were publicly disclosed since July 2021.
Firmware flaws are particularly dangerous because they can lead to malware infections that persist even between OS re-installations or allow long-term compromises that would not trigger standard security tools.
As Binarly highlights in the report, even though it’s been a month since they made some of the flaws public at Black Hat 2022, the vendor hasn’t released security updates for all impacted models, leaving many customers exposed to attacks.
The researchers reported three bugs to HP in July 2021 and the other three in April 2022, so the vendor had between four months and more than a full year to push updates for all affected devices.
Vulnerability details
The flaws Binarly’s security research team discovered recently are all SMM (System Management Module) memory corruption problems leading to arbitrary code execution.
SMM is part of the UEFI firmware that provides system-wide functions like low-level hardware control and power management.
The privileges of the SMM sub-system (ring -2) exceed those of the operating system kernel (ring 0), so flaws impacting the SMM can invalidate security features like Secure Boot, create invisible backdoors (for the victim), and enable intruders to install persistent malware implants.
The six flaws Binarly says HP has left unpatched for months are:
- CVE-2022-23930 – Stack-based buffer overflow leading to arbitrary code execution. (CVSS v3 score: 8.2 “High”)
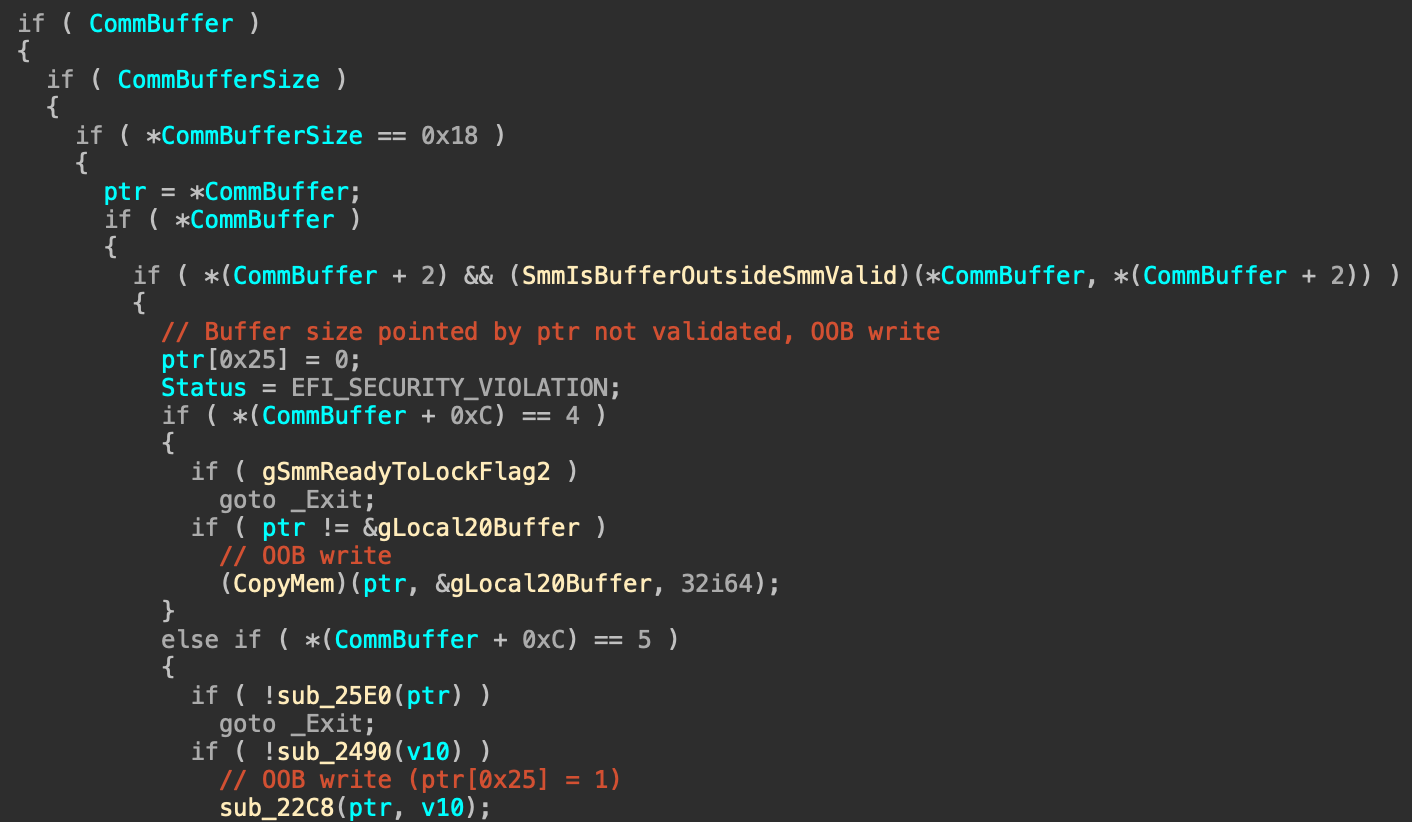
- CVE-2022-31644 – Out-of-bounds write on CommBuffer, allowing partial validation bypassing. (CVSS v3 score: 7.5 “High”)
- CVE-2022-31645 – Out-of-bounds write on CommBuffer based on not checking the size of the pointer sent to the SMI handler. (CVSS v3 score: 8.2 “High”)
- CVE-2022-31646 – Out-of-bounds write based on direct memory manipulation API functionality, leading to privilege elevation and arbitrary code execution. (CVSS v3 score: 8.2 “High”)
- CVE-2022-31640 – Improper input validation giving attackers control of the CommBuffer data and opening the path to unrestricted modifications. (CVSS v3 score: 7.5 “High”)
- CVE-2022-31641 – Callout vulnerability in the SMI handler leading to arbitrary code execution. (CVSS v3 score: 7.5 “High”)
Security flaws fix status
HP has released three security advisories acknowledging the mentioned vulnerabilities, along with an equal number of BIOS updates addressing the issues for some of the impacted models.
CVE-2022-23930 was fixed on all impacted systems in March 2022, except for thin client PCs (check advisory for details).
CVE-2022-31644, CVE-2022-31645, and CVE-2022-31646 received security updates on August 9, 2022.
However, many business notebook PCs (Elite, Zbook, ProBook), business desktop PCs (ProDesk, EliteDesk, ProOne), point of sale systems, and also HP workstations (Z1, Z2, Z4, Zcentral) have not received patches yet (check advisory for details).
CVE-2022-31640 and CVE-2022-31641 received fixes throughout August, with the last update landing on September 7, 2022, but many HP workstations remain exposed without an official fix (check advisory for details).
As Binarly comments, fixing firmware flaws is very challenging for a single vendor due to the complexity of the firmware supply chain, so many HP customers will have to accept the risk and ramp up their physical security measures.
BleepingComputer has contacted HP for a comment on when the security updates for the rest of the impacted models are expected to be released, and we will update this post when we get a response.
Update 9/11/12 11:19 AM EST: This article incorrectly specified that these were HPE vulnerabilities. Modifies to correctly refer to them as HP bugs.