One of the primary methods used by malware distributors to infect devices is by deceiving people into downloading and running malicious files, and to achieve this deception, malware authors are using a variety of tricks.
Some of these tricks include masquerading malware executables as legitimate applications, signing them with valid certificates, or compromising trustworthy sites to use them as distribution points.
According to VirusTotal, a security platform for scanning uploaded files for malware, some of these tricks are happening on a much larger scale than initially thought.
The platform has compiled a report presenting stats from January 2021 until July 2022, based on the submission of two million files daily, illustrating trends in how malware is distributed.
Abusing legitimate domains
Distributing malware through legitimate, popular, and high-ranking websites allows threat actors to evade IP-based blocklists, enjoy high availability, and provide a greater level of trust.
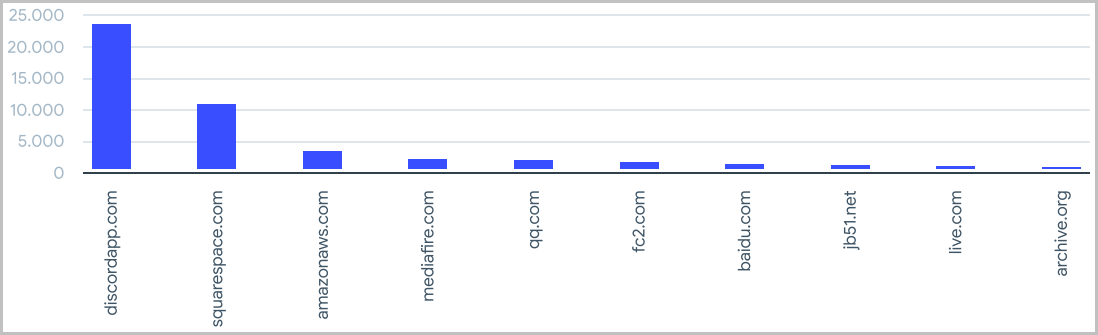
VirusTotal detected 2.5 million suspicious files downloaded from 101 domains belonging to Alexa’s top 1,000 websites.
The most notable abuse case is Discord, which has become a hotbed of malware distribution, with hosting service and cloud service providers Squarespace and Amazon also logging large numbers.
Using stole code-signing certificates
Signing malware samples with valid certificates stolen from companies is a reliable way to evade AV detection and security warnings on the host.
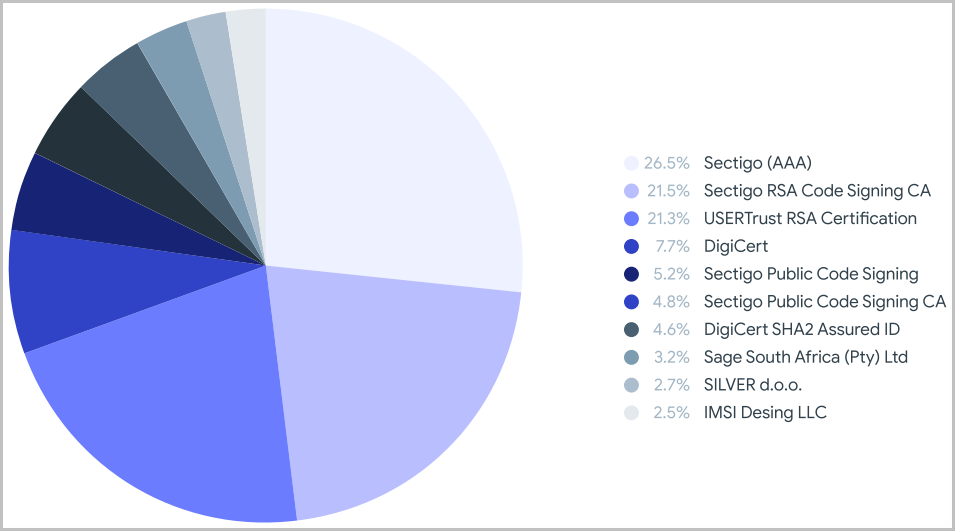
Of all the malicious samples uploaded to VirusTotal between January 2021 and April 2022, over a million were signed, and 87% used a valid certificate.
The most common certification authorities that are used to sign the malicious samples submitted to VirusTotal include Sectigo, DigiCert, USERTrust, and Sage South Africa.
Disguised as popular software
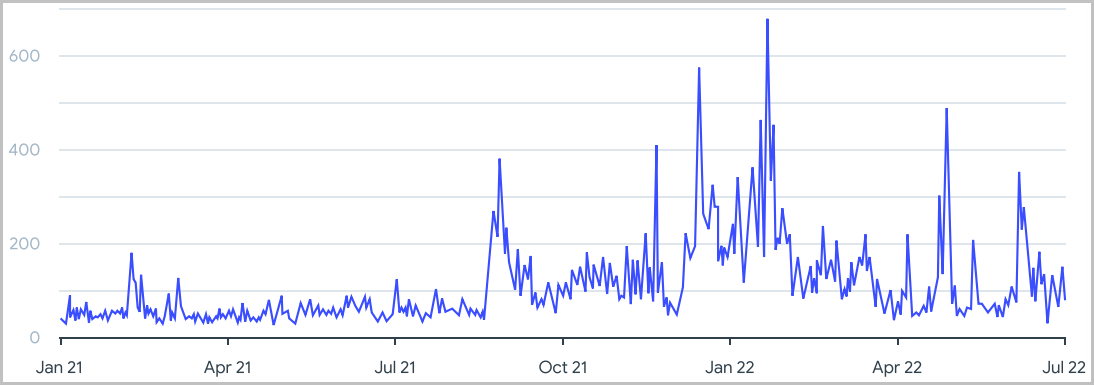
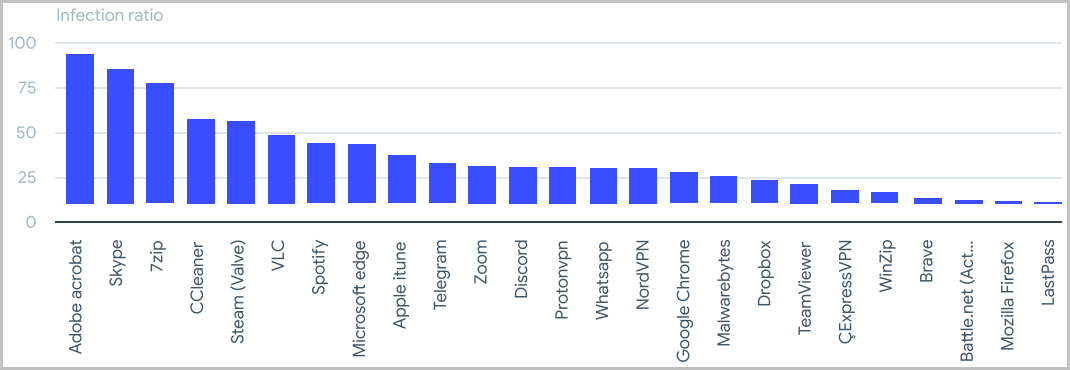
Masquerading a malware executable as a legitimate, popular application has seen an upward trend in 2022.
Victims download these files thinking they’re getting the applications they need, but upon running the installers, they infect their systems with malware.
The most mimicked applications (by icon) are Skype, Adobe Acrobat, VLC, and 7zip.
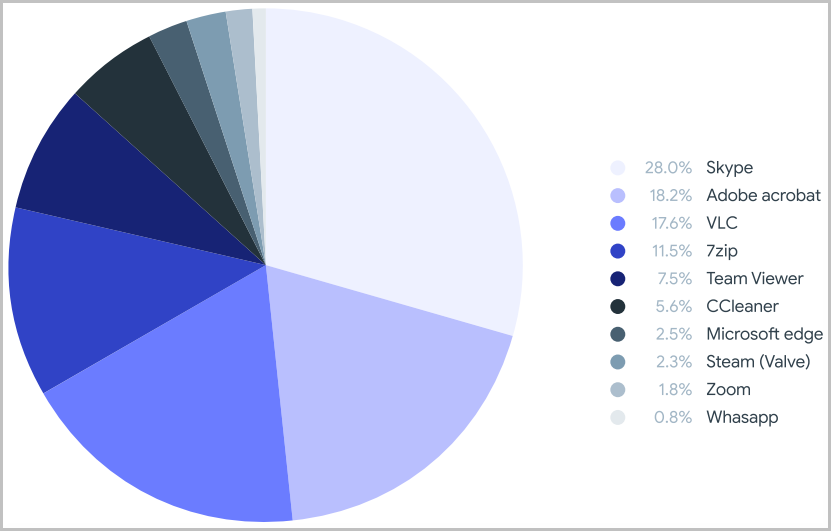
The popular Windows optimization program CCleaner that we saw in a recent SEO poisoning campaign is among the hackers’ prominent choices and features an exceptionally high infection ratio for its distribution volume.
Lacing legitimate installers
Finally, there’s the trick of hiding malware inside legitimate application installers and running the infection process in the background while the real apps execute in the foreground.
This process helps in tricking the victims and also evades some antivirus engines that don’t scrutinize PR resource structure and content in executables.
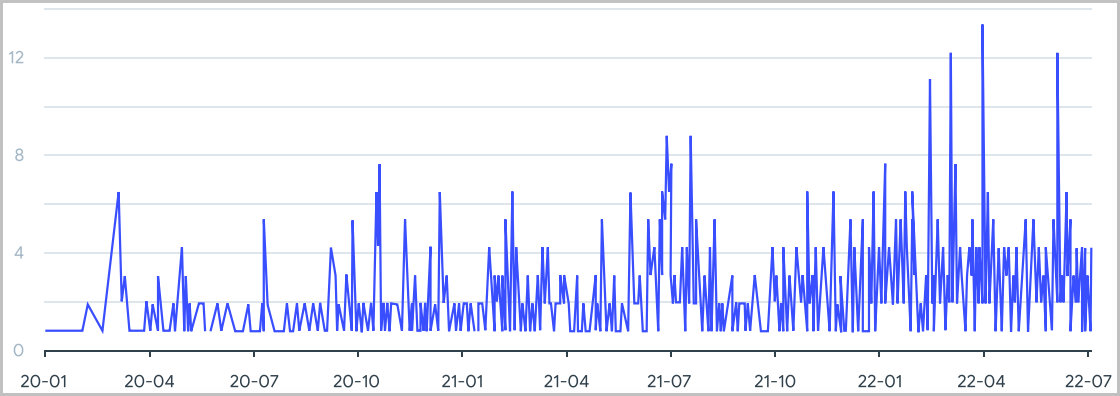
Based on VirusTotal stats, this practice also appears to be on the rise this year, using Google Chrome, Malwarebytes, Windows Updates, Zoom, Brave, Firefox, ProtonVPN, and Telegram as lures.
How to stay safe
When looking to download software, either uses your OS’s built-in app store or visit the application’s official download page. Also, beware of promoted ads on search results that may rank higher as they can easily be spoofed to look like legitimate sites.
After downloading an installer, always perform an AV scan on the file before executing it to ensure they are not malware in disguise.
Finally, avoid using torrent sites for cracks or keygens for copyrighted software, as they commonly lead to a malware infection.










































