This week, ech0raix ransomware has started targeting vulnerable QNAP Network Attached Storage (NAS) devices again, according to user reports and sample submissions on the ID Ransomware platform.
ech0raix (also known as QNAPCrypt) had hit QNAP customers in multiple large-scale waves starting with the summer of 2019 when the attackers brute-forced their way into Internet-exposed NAS devices.
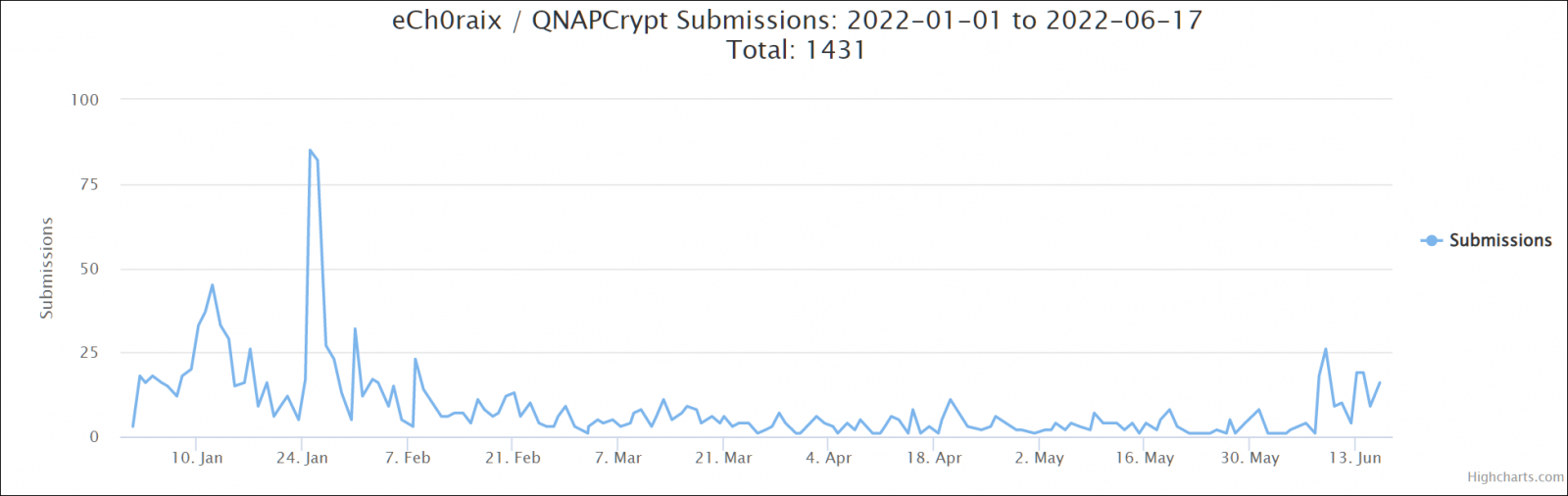
Since then, several other campaigns have been detected and reported by this ransomware strain’s victims, in June 2020, in May 2020, and a massive surge of attacks targeting devices with weak passwords that started in mid-December 2021 (right before Christmas) and slowly subsided towards early February 2022.
A new surge of ech0raix attacks has now been confirmed by a quickly increasing number of ID Ransomware submissions and users reporting being hit in the BleepingComputer forums [1, 2], with the earliest hit recorded on June 8.
Although only a few dozen ech0raix samples have been submitted, the actual number is successful attacks is most likely higher since only some of the victims will use the ID Ransomware service to identify the ransomware that encrypted their devices.
While this ransomware has also been used to encrypt Synology NAS systems since August 2021, victims have only confirmed strikes on QNAP NAS devices this time.
Until QNAP issues more details on these attacks, the attack vector used in this new ech0raix campaign remains unknown.
How to defend your NAS from attacks
While QNAP is yet to issue a warning to alert customers of these attacks, the company has previously urged them to protect their data from potential eCh0raix attacks by:
- using stronger passwords for your administrator accounts
- enabling IP Access Protection to protect accounts from brute force attacks
- and avoiding using default port numbers 443 and 8080
QNAP provides detailed step-by-step instructions on changing the NAS password, enabling IP Access Protection, and changing the system port number in this security advisory.
The Taiwanese hardware vendor has also urged customers to disable Universal Plug and Play (UPnP) port forwarding on their routers to prevent exposing their NAS devices to attacks from the Internet.
You can also follow these step-by-step instructions to disable SSH and Telnet connections and toggle on IP and account access protection.
QNAP also warned customers on Thursday to secure their devices against ongoing attacks deploying DeadBolt ransomware payloads.
“According to the investigation by the QNAP Product Security Incident Response Team (QNAP PSIRT), the attack targeted NAS devices using QTS 4.3.6 and QTS 4.4.1, and the affected models were mainly TS-x51 series and TS-x53 series,” the NAS maker said.
“QNAP urges all NAS users to check and update QTS to the latest version as soon as possible, and avoid exposing their NAS to the Internet.”









































