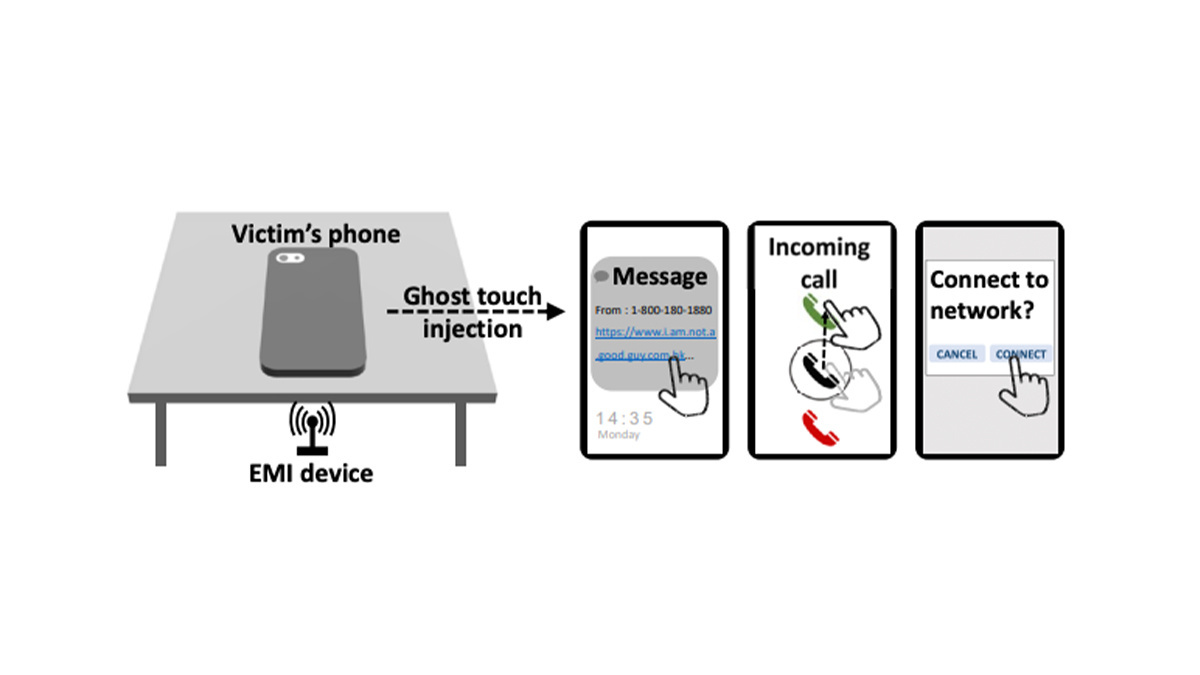
Some attacks on smartphones require physical access to the device and interactions with the touchscreen. So your phone is more or less safe as long as no one touches it, right? Wrong, according to a new research paper by security researchers at Zhejiang University, China, and the Technical University of Darmstadt, Germany.
To be presented at the Usenix Security Symposium in July, the paper (PDF) introduces GhostTouch, a type of attack that can execute taps and swipes on the phone’s screen from a distance of up to 40 millimeters.
According to the researchers’ findings, an attacker can use GhostTouch to carry out several types of malicious actions, including initiating calls and downloading malware.
Electromagnetic interference
Today’s smartphones and tablets use capacitive touchscreens that provide multi-touch capabilities and can measure small electric fields. However, capacitive touchscreens are sensitive to the environmental impact of electromagnetic interference (EMI) and charger noise.
Previous studies show that EMI can disrupt the user experience of touchscreens and possibly cause random and harmful behavior. In one case, a phone that was placed on a charger booked a very expensive hotel room because of EMI signals.
In creating GhostTouch, the researchers wanted to see if they could use EMI to create controllable touch events and trigger arbitrary behavior on capacitive touchscreens.
 The GhostTouch attack in action
The GhostTouch attack in action
Manipulating the touchscreen
The core idea behind GhostTouch is to interfere with the capacitance measurement of touchscreens using electromagnetic signals injected into the receiving electrodes integrated into the touchscreen.
The researchers created a technology stack composed of a waveform generator that creates the EMI signal and an antenna that transmits it to the phone’s touchscreen. A phone locator module determines the exact location of the phone’s screen and calibrates the signals to specific locations.
GhostTouch is a targeted attack. The adversary must know the model and make of the victim’s phone in order to tune the equipment. The attacker might also need extra information about the phone, such as the passcode, which they must acquire through social engineering or ‘shoulder surfing’.
The main scenario for the attack is public places like cafes, libraries, or conference lobbies, where people might place their smartphones face-down on a table. The attacker will have embedded the attack equipment under the table to launch attacks remotely.
The researchers tested several actions with GhostTouch, including answering the phone, pressing a button, swiping up to unlock, and entering a password. For example, if the victim’s phone is on silent mode, an attacker may call the victim and use GhostTouch to answer the call without alarming the victim, and then eavesdrop on a private conversation.
In another scenario, the attacker may send a malicious link to the victim’s phone and use GhostTouch to tap on it and download it.
Testing GhostTouch
The researchers tested GhostTouch on 11 widely used phone models. They were able to use the attack with varying degrees of success on nine models. For example, they were able to establish a malicious Bluetooth connection on an iPhone SE.
The researchers conclude that although the capacitive touchscreens of smartphones go through thorough electromagnetic compatibility tests and include anti-interference design elements, they are still susceptible to EMI attacks such as GhostTouch.
Several countermeasures were proposed, including reinforcing the touchscreen to protect it against targeted EMI attacks and using an algorithms to detect abnormal touch points.










































