Security researchers are warning of an Android malware named SMSFactory that adds unwanted costs to the phone bill by subscribing victims to premium services.
The number of its victims is unclear but attempts to infect Android devices have been recorded for tens of thousands of Android users protected by Avast security products in at least eight countries.
SMSFactory has multiple distribution channels that include malvertising, push notifications, promotional pop-ups on sites, videos promising game hacks or adult content access.
According to Avast, SMSFactory targeted more than 165,000 of its Android customers between May 2021 to May 2022, most of them located in Russia, Brazil, Argentina, Turkey, and Ukraine.
.png)
While SMSFactory’s main goal is to send premium text and make calls to premium phone numbers, Avast researchers noticed a malware variant that can also steal the contact list on compromised devices, likely to be used as another distribution method for the threat.
Jakub Vávra of Avast notes that SMSFactory is hosted on unofficial app stores. ESET researchers found the malicious APK package on APKMods and PaidAPKFree, two Android app repositories that lack vetting and proper security policies for the listed products.
SMSFactory’s stealthy operation
The SMSFactory APK may come under different names and when trying to install it on the device, a warning kicks in from Play Protect – Android’s built-in security system, alerting users about the potential security risk from the file.
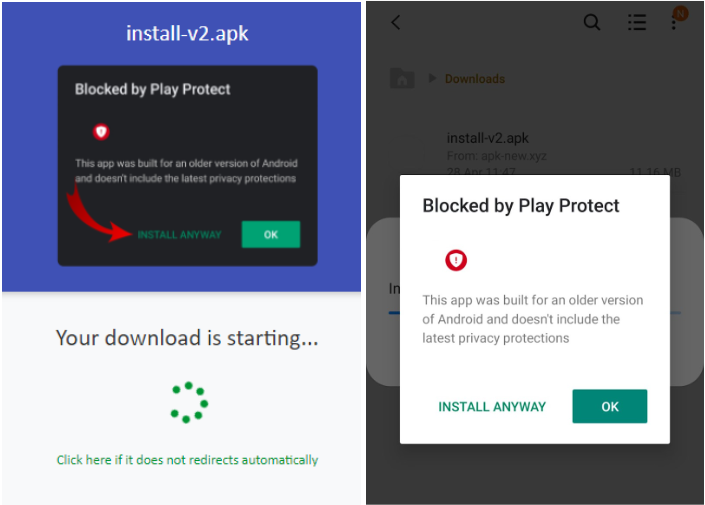
The permissions requested upon installation include accessing location data, SMS, ability to make phone calls and send SMS, wake lock and vibrate, manage overlay, use the entire screen, monitor notifications, and start activities from the background.
These are all permissions indicative of malicious activity, but careless users who look forward to accessing the promised content are likely to allow them without reviewing.
Once installed, the app shows the victim a fake content screen to a service that doesn’t work or is mostly unavailable.
The app itself has no assigned name or icon and can remove the latter from the screen to make more difficult its removal after exiting. As a result, most victims assume that something went wrong with the installation and don’t give another though about the app.
However, SMSFactory continues to operate in the background, establishing a connection to the command and control (C2) server and sending an ID profile of the infected device.
If the campaign operators deem the device usable, they send back instructions and subscribe the victim to premium services.
One of the most recent variants of the SMSFactory malware can also add admin accounts on the device, likely required for the SMS distribution using the contact list.
How to stay safe
To avoid larger bills, users are recommended to download apps only from trusted sources, such as Google Play. They should keep at a minimum the number of applications they’re using and read reviews from other users before installing anything.
Additionally, keep your operating system updated to the latest available version for your device and run regular scans via Play Protect.
For malware that subscribes to premium services, some carriers offer the option to disable or limit this action.










































