Kaspersky’s quarterly report on mobile malware distribution notes a downward trend that started in late 2020. Despite the overall demise in malware volumes, the security company reports a spike in trojan distribution, including generic trojans, banking trojans, and spyware.
This worrying development underlines an increasing focus on more sophisticated and damaging operations that gradually replace the low-yielding adware and “risk-tools”.
.png)
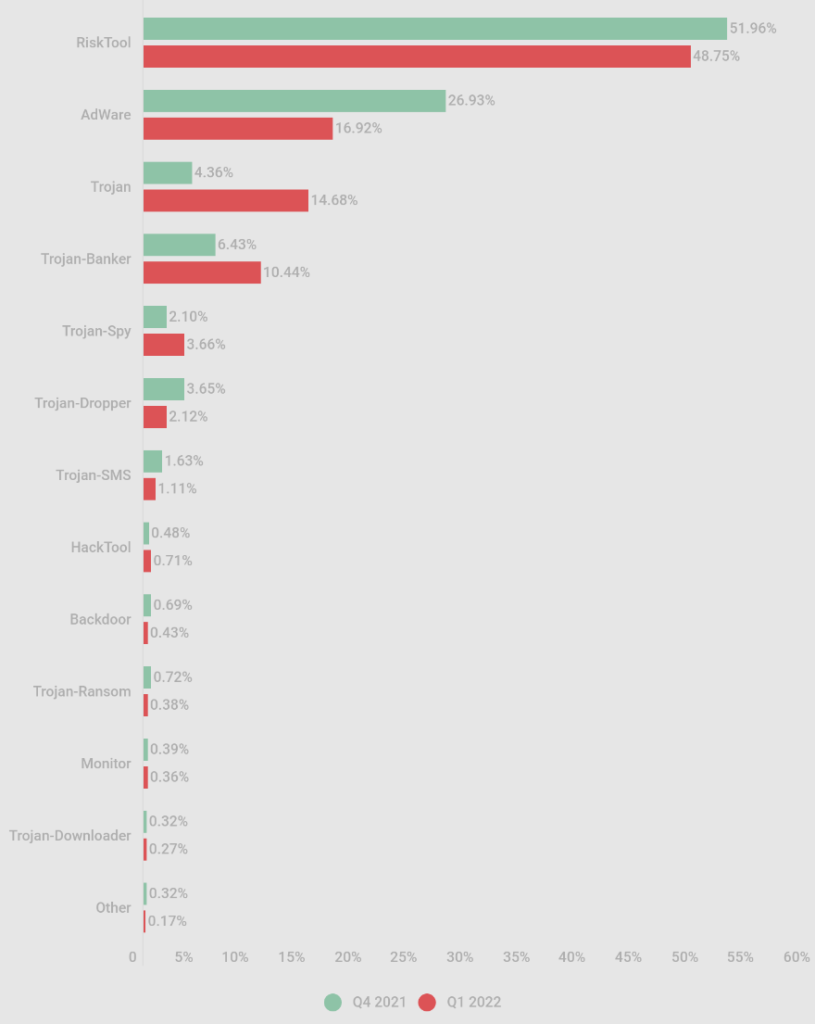
Adware and “risk tools” remain the most prevalent in terms of distribution volumes, with the latter accounting for almost half of all mobile malware infection attempts detected by Kaspersky in Q1 2022.
Rising trojans
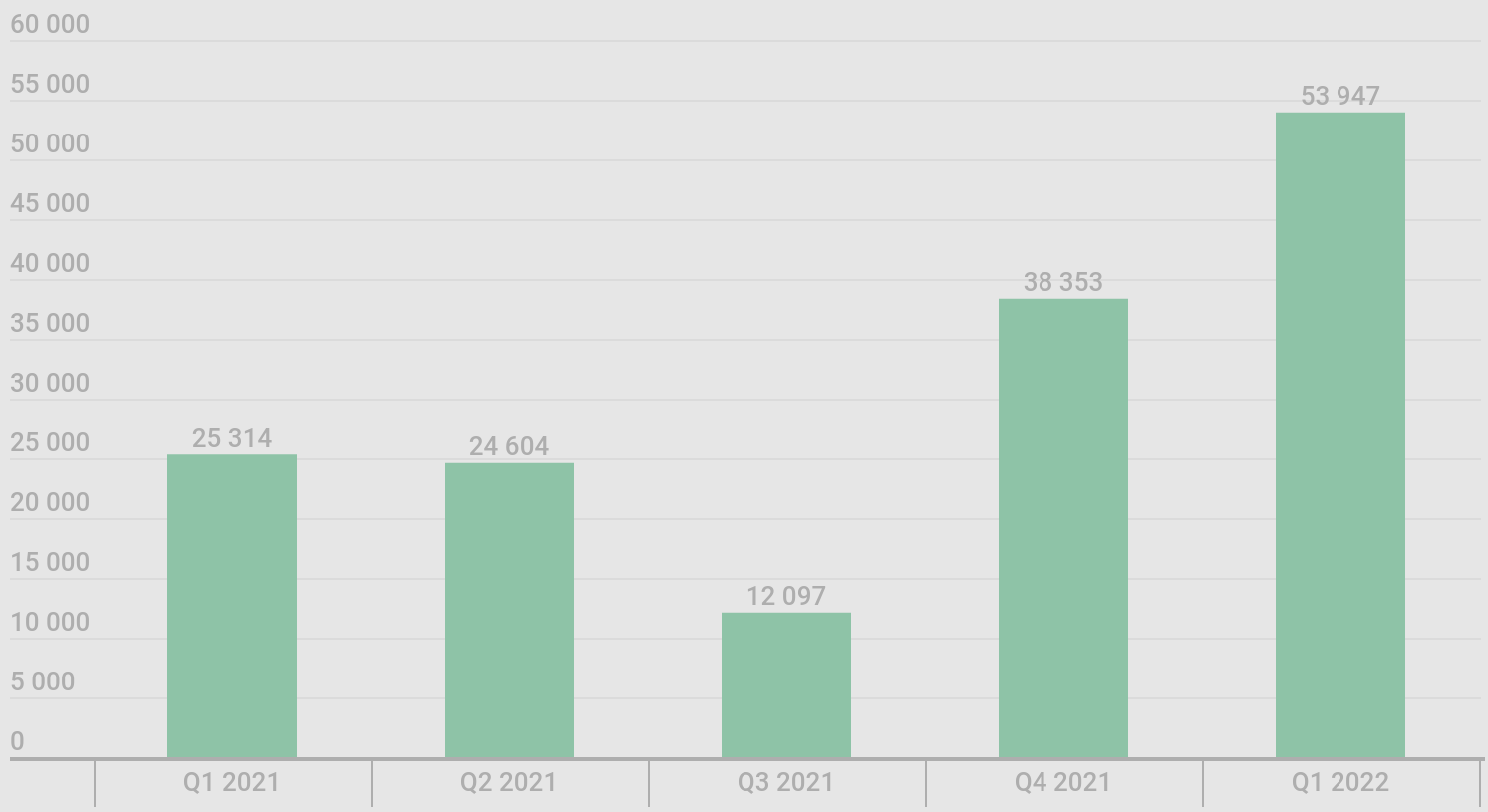
Detections for mobile banking trojans have increased by about 40% compared to the previous quarter, and the number doubled compared to Q1 2021 data.
This type of malware typically overlays login screens on top of legitimate banking or cryptocurrency management apps to steal people’s account credentials.
Banking trojans are becoming more widely and cheaply available on hacking forums and Telegram channels, so their adoption by low-skill cyber-criminals increases.
According to Kaspersky, the new family that pushed the distribution figures upwards this quarter is the one they track as “Trojan-Banker.AndroidOS.Bray”, which accounted for 81% of all mobile trojan detections in the first quarter of the year.
Highlighted Q1 2022 threats
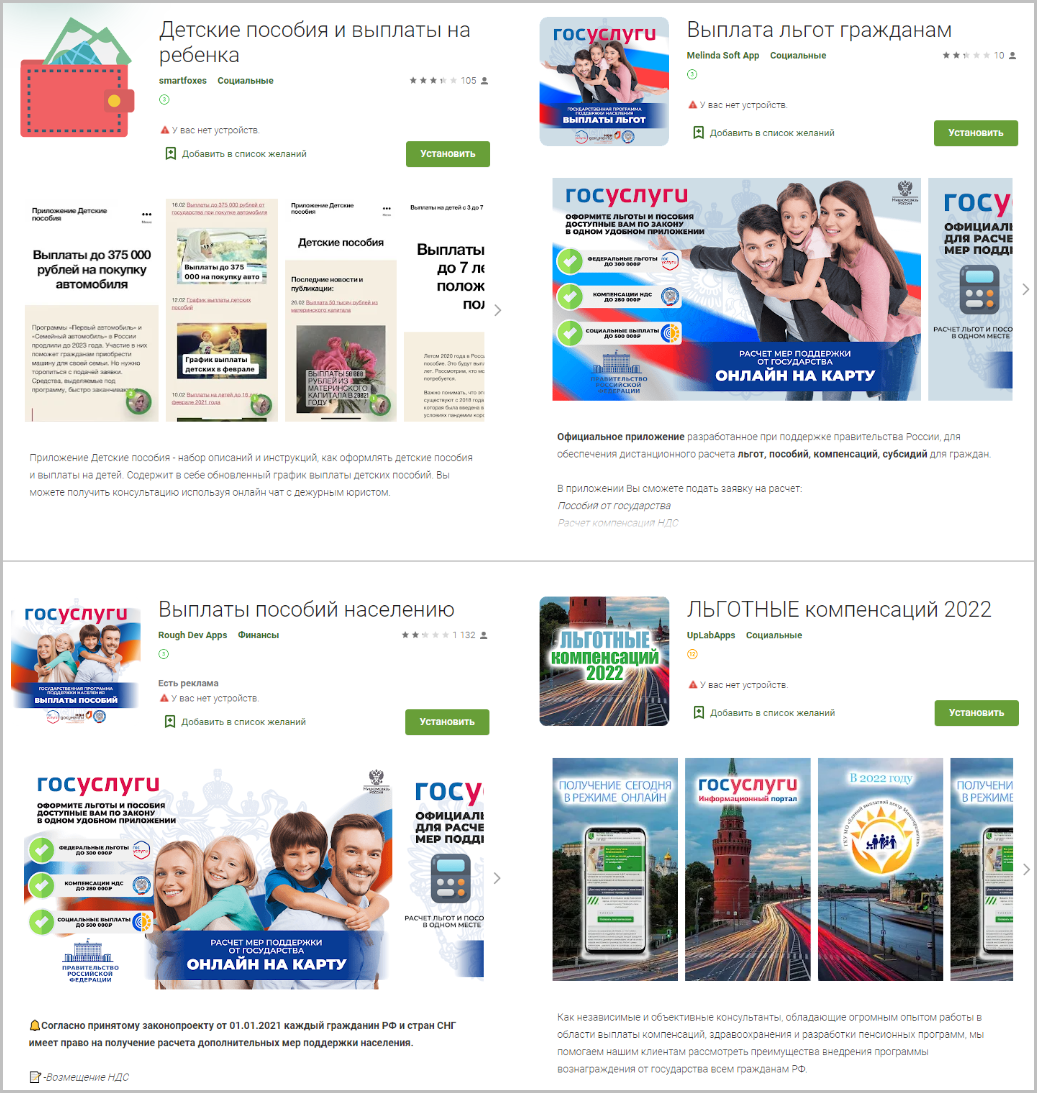
Kaspersky has noticed some interesting trends at the start of this year, the most notable being a rise in fraud apps pushed via official app store channels such as Google’s Play Store.
In the first quarter of 2022, scammers exploited the Russian invasion of Ukraine to offer fake public benefit apps promising financial assistance in response to sanctions and transactional restrictions. Yet, these apps simply stole users’ money by directing them to external, malicious websites.
Another highlighted threat is aggressive payday loan applications that target mainly users in India, Brazil, and Mexico.
Kaspersky classifies these as “RiskTool.AndroidOS.SpyLoan”, and says these apps request access to the user’s contact lists, SMS, and photos during installation. If the payment is late, this information is used for extortion.

In some cases, it has been reported that debt collecting agents working for these platforms call people from the users’ contact lists to expose them and increase the pressure to pay the debt.
In other, even more extreme cases, the users of these applications are locked out of their phones if they miss a payment, echoing ransomware threats.
Q2 2022 Outlook
The developments and conditions that fueled trends unfolding in the last quarter remain unchanged, so trojan distribution is expected to continue substituting threats tagged as adware and riskware.
Mobile devices are often a weak link in the security chain, and their presence into corporate environments continues rise. Unfortunately, this is not always done with proper security measures.
Both Google and Apple have come a long way when it comes to implementing protections, mechanisms to protect against permission abuse, and making their app stores safer; but malicious actors still manage to attack users.
All that said, users should keep their devices up to date, install the minimum required number of applications and only from the official stores, scrutinize the requested permissions, read user reviews, review the developer’s site, and use mobile security tools.









































