A malspam campaign has been found distributing the new META malware, a new info-stealer malware that appears to be rising in popularity among cybercriminals.
META is one of the novel info-stealers, along with Mars Stealer and BlackGuard, whose operators wish to take advantage of Raccoon Stealer’s exit from the market that left many searching for their next platform.
Bleeping Computer first reported about META last month, when analysts at KELA warned about its dynamic entrance into the TwoEasy botnet marketplace.
The tool is sold at $125 for monthly subscribers or $1,000 for unlimited lifetime use and is promoted as an improved version of RedLine.
New Meta malspam campaign
A new spam campaign seen by security researcher and ISC Handler Brad Duncan is proof that META is actively used in attacks, being deployed to steal passwords stored in Chrome, Edge, and Firefox, as well as cryptocurrency wallets.
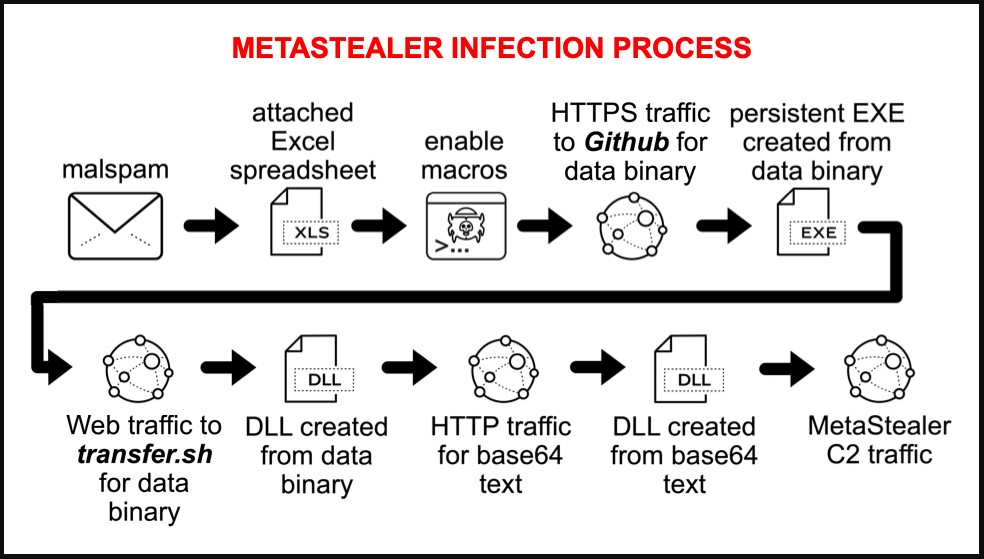
The infection chain in the particular campaign follows the “standard” approach of a macro-laced Excel spreadsheet arriving in prospective victims’ inboxes as email attachments.
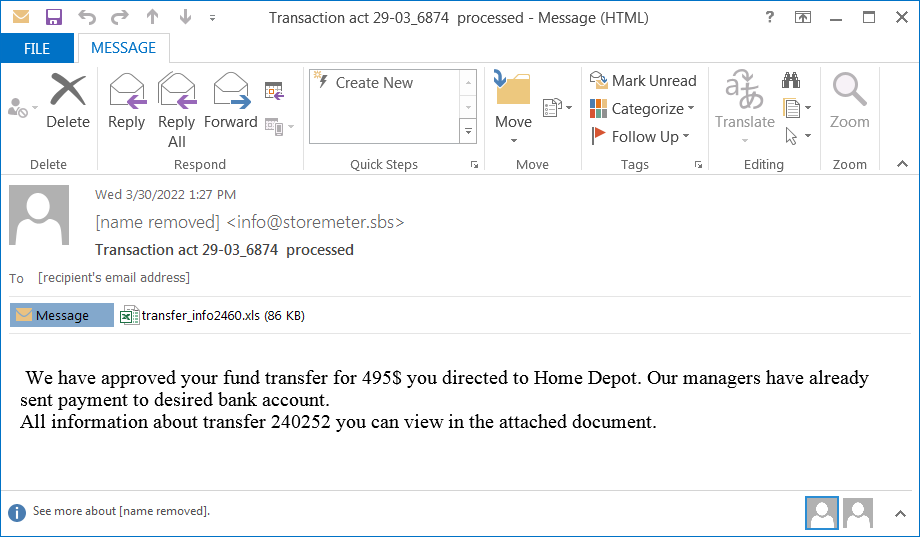
The messages make bogus claims of fund transfers that are not particularly convincing or well-crafted but can still be effective against a significant percentage of recipients.
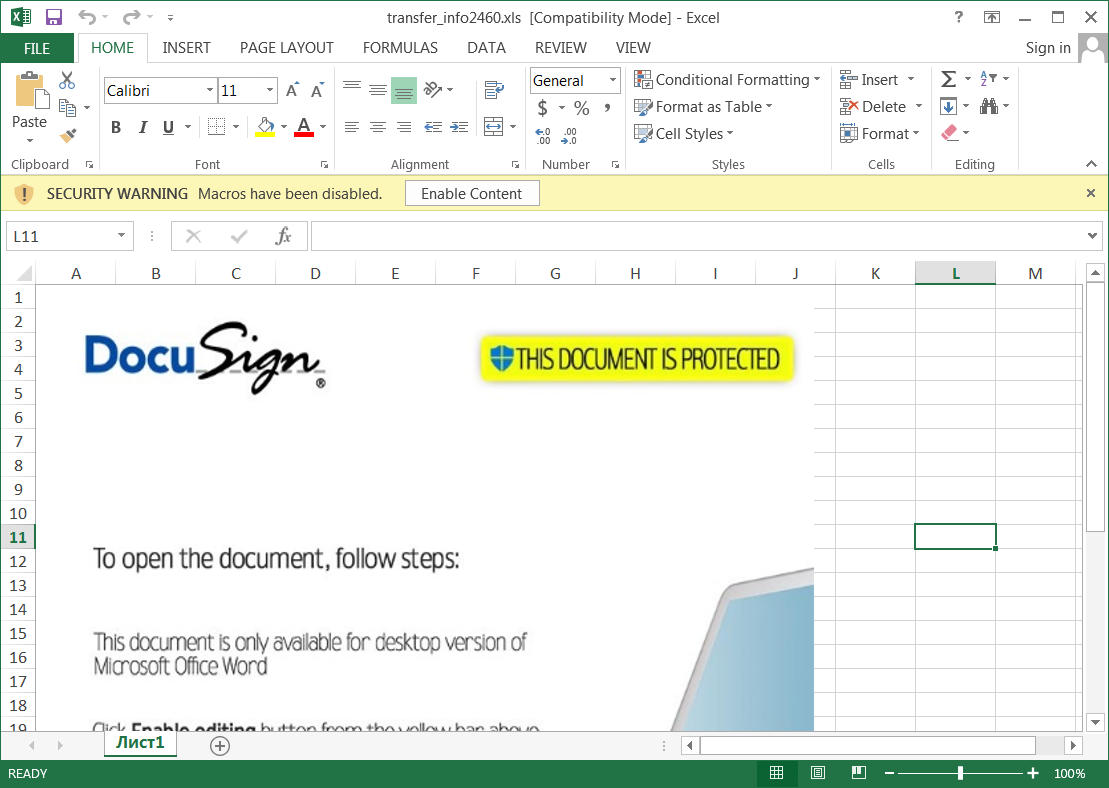
The spreadsheet files feature a DocuSign lure that urges the target to “enable content” required to run the malicious VBS macro in the background.
When the malicious script runs, it will download various payloads, including DLLs and executables, from multiple sites, such as GitHub.
Some of the downloaded files are base64 encoded or have their bytes reversed to bypass detection by security software. For example, below is one of the samples collected by Duncan that has its bytes reversed in the original download.
.png)
Eventually, the final payload is assembled on the machine under the name “qwveqwveqw.exe,” which is likely random, and a new registry key is added for persistence.
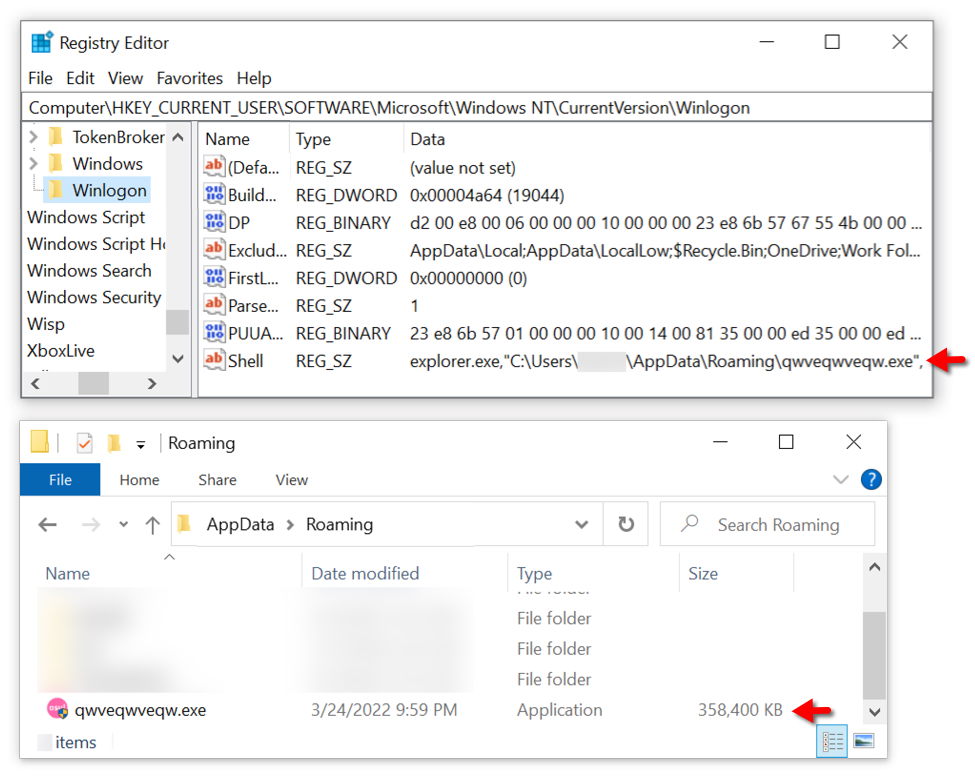
A clear and persistent sign of the infection is the EXE file generating traffic to a command and control server at 193.106.191[.]162, even after the system reboots, restarting the infection process on the compromised machine.
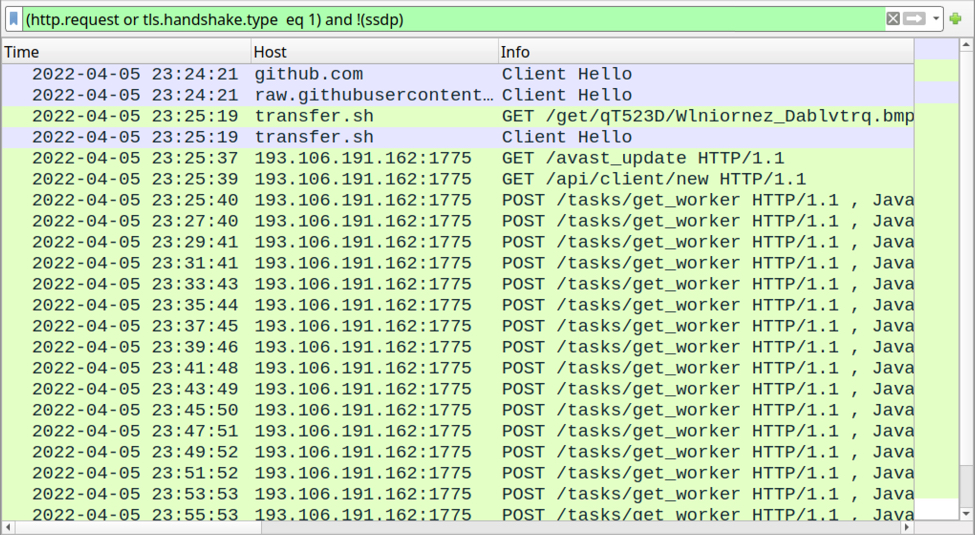
One thing to note is that META modifies Windows Defender via PowerShell to exclude .exe files from scanning, to protect its files from detection.
If you’d like to dive deeper into the malicious traffic details for detection purposes or curiosity, Duncan has published the PCAP of the infection traffic here.









































