Research into the hacking techniques that result in companies being infected with ransomware offers organizations some useful pointers towards how best to avoid this increasingly common form of cyber-attack.
Ransomware attacks have grown at an alarming rate over the last few years, driven by the proliferation in strains of malware and the emergence of affiliate programs that bring less skilled cybercriminals into play, among other factors.
The basic scam – breaking into systems and encrypting data before extorting victims into paying for decryption keys – is so lucrative (partly because of the growing utility and value of cryptocurrencies) that it has fueled development of a diverse and growing cybercrime ecosystem.
Setting the scene
Analytical research from Security Scorecard, presented at the VB2021 security conference last week, reports that 20 different ransomware families threaten to publicly expose the data belonging to companies that are unwilling to pay the ransom cybercriminals demand.
Attackers typically use Tor domains to disclose the identity of the companies they’ve infected as well as to upload files they’ve stolen before starting the encryption process.
Researchers from US-based Security Scorecard scoured Tor websites maintained by the attackers in order to gain intelligence on attacks against non-paying victims.
The firm looked at ransomware-linked data leak websites to gather a list of companies known to have been victims of ransomware.
Happy families?
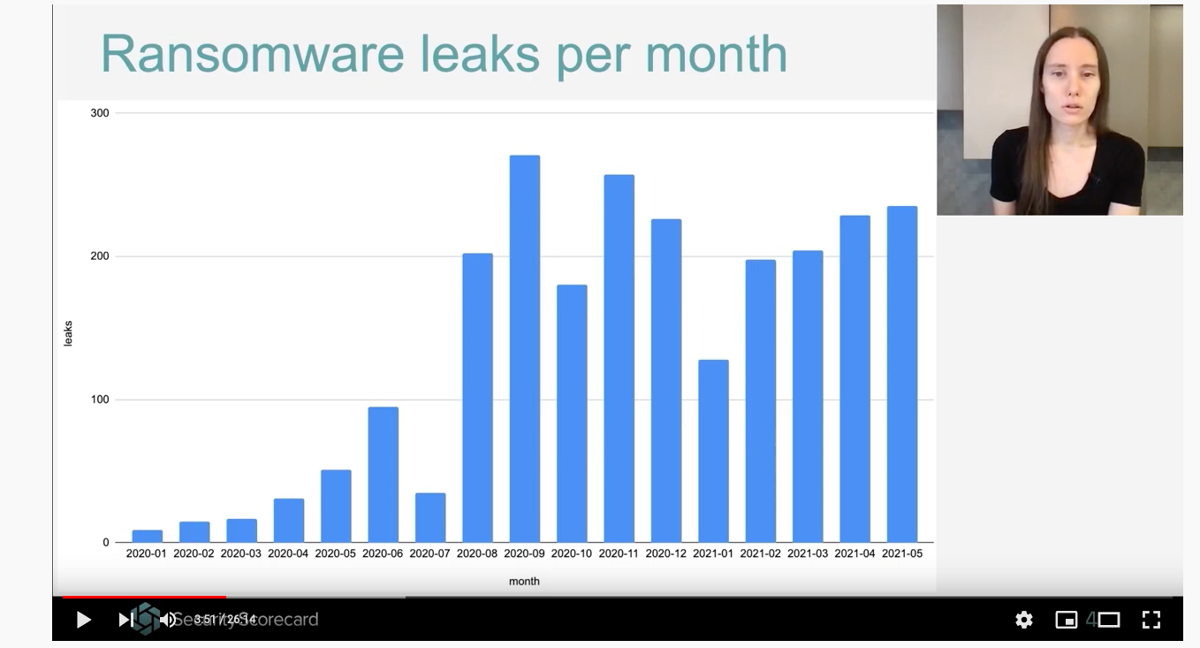
Around 750 companies had their data leaked following ransomware infection between March and May 2021, according to work by the Security Scorecard team.
Conti, Avaddon, and REvil were the most common vectors of these leaks but several other ransomware families were involved too.
 The number of ransomware attacks continues to skyrocket
The number of ransomware attacks continues to skyrocket
The same researchers sinkholed unused command and control domains tied to particular ransomware families in order to get a secondary source of data for active ransomware attacks.
Ransomware infects systems through other malware families or exploit kits, exposed network services, software vulnerabilities, and spam campaigns proffering malware-tainted messages, among other techniques.
For example, infections by the Emotet malware are “highly correlated” with ransomware infections, a finding researchers reached after analyzing network traffic sent to malware command and control servers.
Cobalt Strike – a legitimate pen testing tool with dual use capabilities – is frequently used by ransomware authors, according to Security Scorecard.
“By correlating the victims of these malware families and exploit kits, the entities running these vulnerable services, as well as the entities that have poor email hygiene with the victims of ransomware attacks, we can estimate the risk those exposures added to the probability of ransomware infection,” said the firm.
The Daily Swig asked Security Scorecard a number of questions about its research but we’re yet to hear back from the researchers. We’ll update this story as and when more information comes to hand.










































