The zero-day vulnerability used to breach on-premise Kaseya VSA servers was in the process of being fixed, just as the REvil ransomware gang used it to perform a massive Friday attack.
The vulnerability had been previously disclosed to Kaseya by security researchers from the Dutch Institute for Vulnerability Disclosure (DIVD), and Kaseya was validating the patch before they rolled it out to customers.
However, in what can only be seen as a case of bad timing, the REvil ransomware gang beat Kaseya and used the same zero-day to conduct their Friday night attack against managed service providers worldwide and their customers.
“After this crisis, there will be the question of who is to blame. From our side, we would like to mention Kaseya has been very cooperative. Once Kaseya was aware of our reported vulnerabilities, we have been in constant contact and cooperation with them. When items in our report were unclear, they asked the right questions,” said DIVD Victor Gevers in a blog post today.
“Also, partial patches were shared with us to validate their effectiveness. During the entire process, Kaseya has shown that they were willing to put in the maximum effort and initiative into this case both to get this issue fixed and their customers patched.”
“They showed a genuine commitment to do the right thing. Unfortunately, we were beaten by REvil in the final sprint, as they could exploit the vulnerabilities before customers could even patch.”
Kaseya has confirmed with BleepingComputer that they are working closely with DIVD.
Little is known about the zero-day
The zero-day Kaseya vulnerability was discovered by DIVD researcher Wietse Boonstra and was assigned the CVE-2021-30116 identifier.
When questioned regarding how REvil learned of the vulnerability as it was being fixed, Gevers indicated in a tweet that the vulnerability was simple to exploit.
Gevers told BleepingComputer that the vulnerability disclosure was “within the industry-standard time for coordinated vulnerability disclosure,” and they would provide more information in a future advisory.
In our queries to Kaseya about the disclosure timeline, they told us that they were not providing any further information at this time.
Only 140 publicly accessible VSA servers
Since the onset of the attacks, DIVD researchers have been providing a list of publicly accessible VSA IP addresses and customer IDs to Kaseya to get the servers offline.
This effort has led to a dramatic decrease in publicly accessible servers, with only 140 accessible today.
“During the last 48 hours, the number of Kaseya VSA instances that are reachable from the internet has dropped from over 2.200 to less than 140 in our last scan today,” said Gevers in a Tweet.
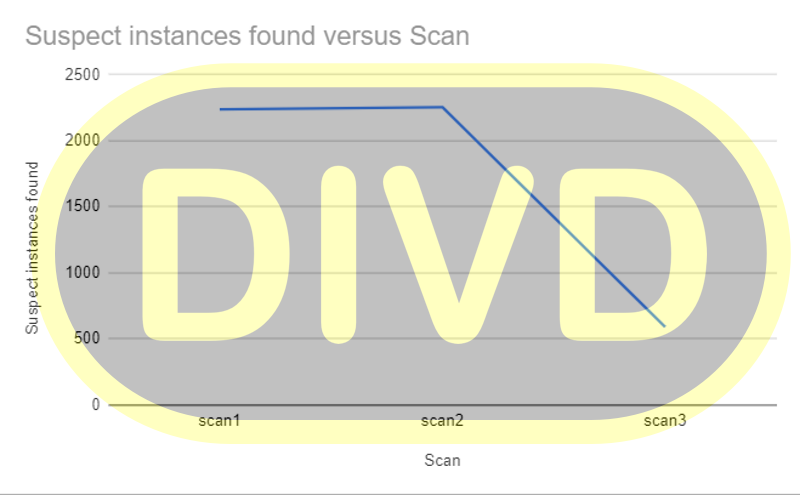
Source: DIVD
In yesterday’s status report from Kaseya, these efforts appear to be working as there was only one further report of a compromised VSA on-premise server.
Furthermore, Gevers reports that they have successfully removed all public access to Kaseya VSA servers in the Netherlands.
In a new update by Kaseya, it is recommended that all VSA on-premise servers remain offline until a patch is released.
Kaseya is also in the process of bringing their SaaS servers farms online and coming up with a plan for hosted VSA servers.