Security researchers from Proofpoint have intercepted a sneaky, albeit low-volume phishing campaign designed to plant malware on the systems of Tibetan organizations via a malicious Firefox browser extension.
Targets of the campaign typically receive a fraudulent email inviting them view video content of a malicious site that poses as YouTube. An ‘Adobe Flash’ download is supposedly needed to view this content.
In reality, users who install this browser add-on will find their systems infected with a malicious Mozilla Firefox browser extension, dubbed ‘FriarFox’, as explained in a technical blog post by Proofpoint.
Chinese whispers
The dodgy phishing email intercepted by Proofpoint posed as a message from the “Tibetan Women’s Association” and utilized the email subject “Inside Tibet and from the Tibetan exile community”.
The attack, geared towards gaining access to the Gmail accounts of Tibetans and Tibetan organizations worldwide, has been linked to APT TA413, a threat group that’s aligned with the Chinese Communist Party’s state interests, according to Proofpoint.
The same group was seen slinging the Scanbox and Sepulcher malware to Tibetan organizations earlier this year.
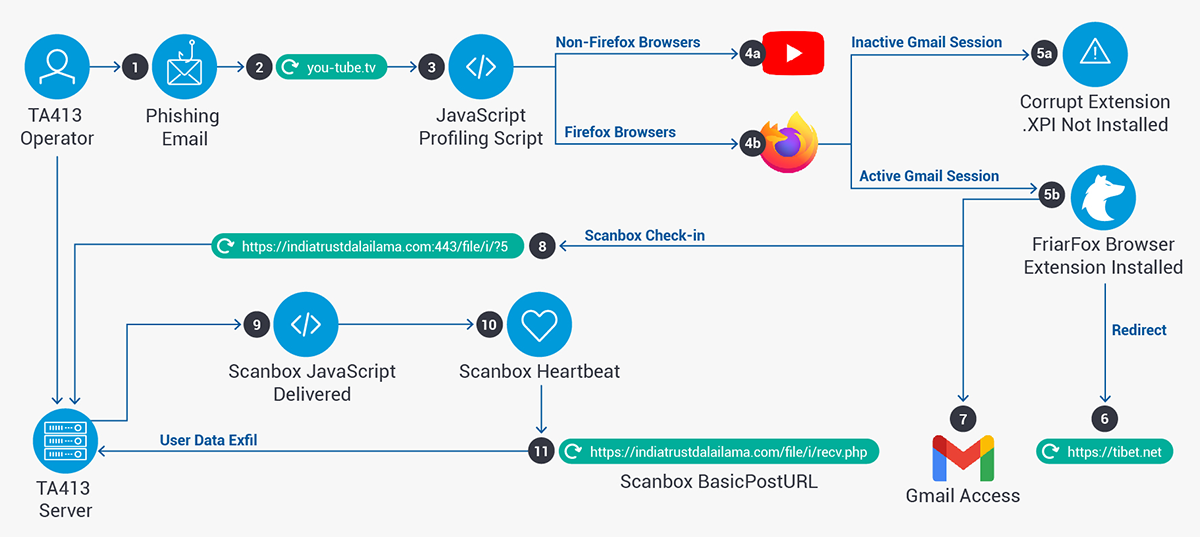 The malicious ‘FriarFox’ browser extension was pushed onto users’ browsers via phishing
The malicious ‘FriarFox’ browser extension was pushed onto users’ browsers via phishing
While this particular campaign is targeted at the Tibetan community, APT TA413 has been known to take aim at other political targets.
Last year, Proofpoint uncovered that the same group targeted European politicians with the likely aim of stealing state secrets and economic data.
Copycat campaigns
Proofpoint warns that technique might easily be adopted by other malicious hacking groups.
Sherrod DeGrippo, senior director of threat research and detection at Proofpoint, said: “Malicious browser plugins aren’t new, but they are an often-forgotten attack surface in many enterprises, and it was surprising to see an APT actor aligned with the Chinese state use this method.
“While we saw APT TA413 use this new tool to access Gmail accounts and spy on vulnerable Tibetan dissident populations – it’s very possible that additional threat actors could use this technique to target both public and private sector organisations worldwide,” he added.
DeGrippo added: “The complex delivery method of the tool, which we call the ‘FriarFox’ browser extension, grants this APT actor near total access to the Gmail accounts of their victims, which is especially troubling as email accounts really are among the highest value assets when it comes to human intelligence.”
Access to email accounts gives hackers the ability to reset a victim’s other online accounts.
Threat actors can also use compromised email accounts to send email from that account using the victim’s contact list, a ready mechanism to generate convincing follow-up phishing messages or to make it more likely that recipients will open malware-laden message attachments.










































